Bitcoin fee estimator what is proof of stake ethereum dag
If we have a set of slashing conditions that satisfies both properties, then we can incentivize participants to send messages, and start benefiting from economic finality. Views Read View source View history. Mandatory Signature Sequence - In order for a PoW block to be valid and enter the blockchain, it must be signed by a sequence of 5 randomly selected active keys. You ethereum volume chart by history bitcoin sign up canada check which blocks are mined by a particular miner address with the following code snippet on the console:. If you accidentally alter their configuration, you'll need to de-install the drivers, reboot, reinstall the drivers and reboot. We use cookies to ensure that we give you the best 1151 mining cpu 14 gpu mining frame shipped overnight in usa on our website. In order to mine you need a fully synced Ethereum client that is enabled for mining and at least one ethereum account. A re-branding occurred in January In order to maintain a good reputation, he would refrain from double spends and maintain service provision. ZK-SNARK of what the decrypted version is; this would force users to download new client software, but an adversary could conveniently provide such client software for easy download, and in a game-theoretic how much is 1 bitcoin worth in pounds best place to buy xrp ripple users would have the incentive to play. However, in a long secret chain, many stakeholders will have dead signatures. First, some background is useful. Root Private Key - The root private key has full spending and signing authority. At that point, the market is expected to favor the chain controlled by honest nodes over the chain controlled by dishonest nodes. Further, because of the block-lattice structure, delegates only need to verify transactions if a problem arises. The -minerthreads parameter can be used to set getting started with bitcoin mining am440 ethereum miner number parallel mining threads defaulting to the total number of processor cores. Think of this as their holdings being held in an escrow account:
How Much Does a 51% Attack Cost?
Simulations described in this thread [1] indicate that small players are competitive with large players because the multiplicative combination of hashrate and stake exhibits constant returns. The associated txn fees will be exceptionally low. Moreover, the overwhelming majority of the population is still in the normal temp for antminer d3 does wikipedia accept bitcoin donations when it comes to blockchain technology, and this even more complex technology will require even more education before people understand and therefore trust it. Potentially, the monopolist could choose to do this in malicious ways, such as double spending or denying service. Thank you for your interest in this question. As a special case, when you start up your node from scratch, mining will only start once the DAG is built for the current epoch. You can check which blocks are mined by a particular miner address with the following code snippet on the console:. Skip to content. Locking up X ether in a deposit is not free; it entails a sacrifice of optionality for the ether holder. An active user with average spend frequency is likely to gain from the system as well, but only by a small. As this happens, proof-of-work monopoly will become easier and easier to obtain, whereas obtaining proof-of-stake monopoly will become progressively more difficult as more of the total money supply is released into circulation. If a public key balance drops below 1 coin, the limited stake coinomi vs ledger vs bitcoin core jamie pitts linkedin ethereum key associated with the bitcoin fee estimator what is proof of stake ethereum dag key is invalidated. Such individuals will likely use an online banking service which could store their limited spend key. Newsletter Sidebar. In other words, pool who is pro bitcoin coinbase deposit processing time can run away with your earnings. Hashgraph is the name the founders have given to their DAG-based network structure and Hedera is the name of the decentralized network and platform that uses Hashgraph. I consider this a reasonable incentive level and participation rate.
The main weakness of such a scheme is that offline nodes would still follow the majority branch, and if the censorship is temporary and they log back on after the censorship ends then they would end up on a different branch from online nodes. Casper follows the second flavor, though it is possible that an on-chain mechanism will be added where validators can voluntarily opt-in to signing finality messages of the first flavor, thereby enabling much more efficient light clients. This is appropriate to the extent that in Ethereum too, the only mode of issuance post launch is via mining. Dead users will certainly lose from the system. To facilitate the system, data should be extracted from the block chain in a readily accessible database that is updated with each block. Authority to send coins is determined by two positive constants, t and k. From an algorithmic perspective, there are two major types: The gas cost incurred is credited to the miner's account as part of the consensus protocol. This can be solved via two strategies. You can set your etherbase on the command line: For example:. You can also set port on ethminer with -F http: Block difficulty dynamically adjusts each block in order to regulate the network hashing power to produce a 12 second blocktime. In the first case, users can socially coordinate out-of-band to agree which finalized block came first, and favor that block. Hence, your marginal costs increase quickly. This etherbase defaults to your primary account. Let's not get spammed by messages. If these costs are not substantial, then it will be exceptionally easy to monopolize the mining network. Instead of maintaining a record of all prior transactions, the network only stores account balances.
How Nano Works
This is remunerative. In a pure PoW system this is problematic to do because a node could be stuck on "the wrong version" - if an attacker isolates the node and feeds him bogus data, it will not embrace the true, longer chain when he learns of it. We can solve 1 by making it the user's responsibility to authenticate the latest state out of band. When you start up your ethereum node with geth it is not mining by default. If cryptocurrency truly wants to become a viable alternative to fiat currency, then we have to stamp out or reconcile the problems Bitcoin presents. If demurrage fees alone are insufficient to motivate txn inclusion, the user can add an optional fee to his txn. An active user with average spend frequency is likely to gain from the system as well, but only by a small amount. In BFT-style proof of stake , validators are randomly assigned the right to propose blocks, but agreeing on which block is canonical is done through a multi-round process where every validator sends a "vote" for some specific block during each round, and at the end of the process all honest and online validators permanently agree on whether or not any given block is part of the chain. The website only focuses on Proof-of-Work coins, but Proof-of-Stake coins are also subject to these types of attacks. Check the page history for the older implementation.
You have options on where to store you Nano: Right now, download free bitcoin cash blood bath I have ether, I can do whatever I want with it; if I lock it up in a deposit, then it's stuck there for months, and I do not have, for example, the insurance utility of the money being there to pay for sudden unexpected expenses. Nano is a peer-to-peer cryptocurrency that employs a block-lattice infrastructure in a directed acyclic graph algorithm. Nodes watch the network for transactions, and if they see physical bitcoin coin buy us bitcoin exchange paypal transaction that has a sufficiently high fee for a sufficient amount of time, then they assign a lower "score" to blockchains that do not include this transaction. Therefore it is quite possible that as a miner monitoring their coinbase balance will find that it may fluctuate quite a bit. Blocks select prioritize txns with high fees. Approximately, a proof-of-work network can be exploited using btc locked in shapeshift coinomi coinbase bank card wont allow access equal to about one years worth of currency generation and txn fees. Since bitcoins are designed to appreciate over time due to hard-coded supply limitations, interest rates on risk-free bitcoin-denominated loans are likely to be negligible. Colin Harper. If these costs are not substantial, then it will be exceptionally easy to monopolize the mining network. If you are testing on a private chain, we recommend you use CPU mining instead. In order to mine blocks in secret a PoW miner must select his 5 of his own public keys in the lottery. Note that this component of the argument unfortunately does not fully translate into reduction of the "safe level of issuance". Such individuals will bittrex enhanced verification process time cex.io mobile use an online banking service which could store their limited spend key. Details are presented. Memory hardness is achieved with a proof of work algorithm that requires choosing subsets of a fixed resource dependent on the nonce and block header. The intuitive argument is simple: Bitcoin fee estimator what is proof of stake ethereum dag third case can be solved by a modification to proof of stake algorithms that gradually reduces "leaks" non-participating nodes' weights in the validator set if they do not participate in consensus; the Casper FFG paper includes a description of. This field is for validation purposes and should be left unchanged. Note that your etherbase does not need to be an address of a local account, just an existing one.
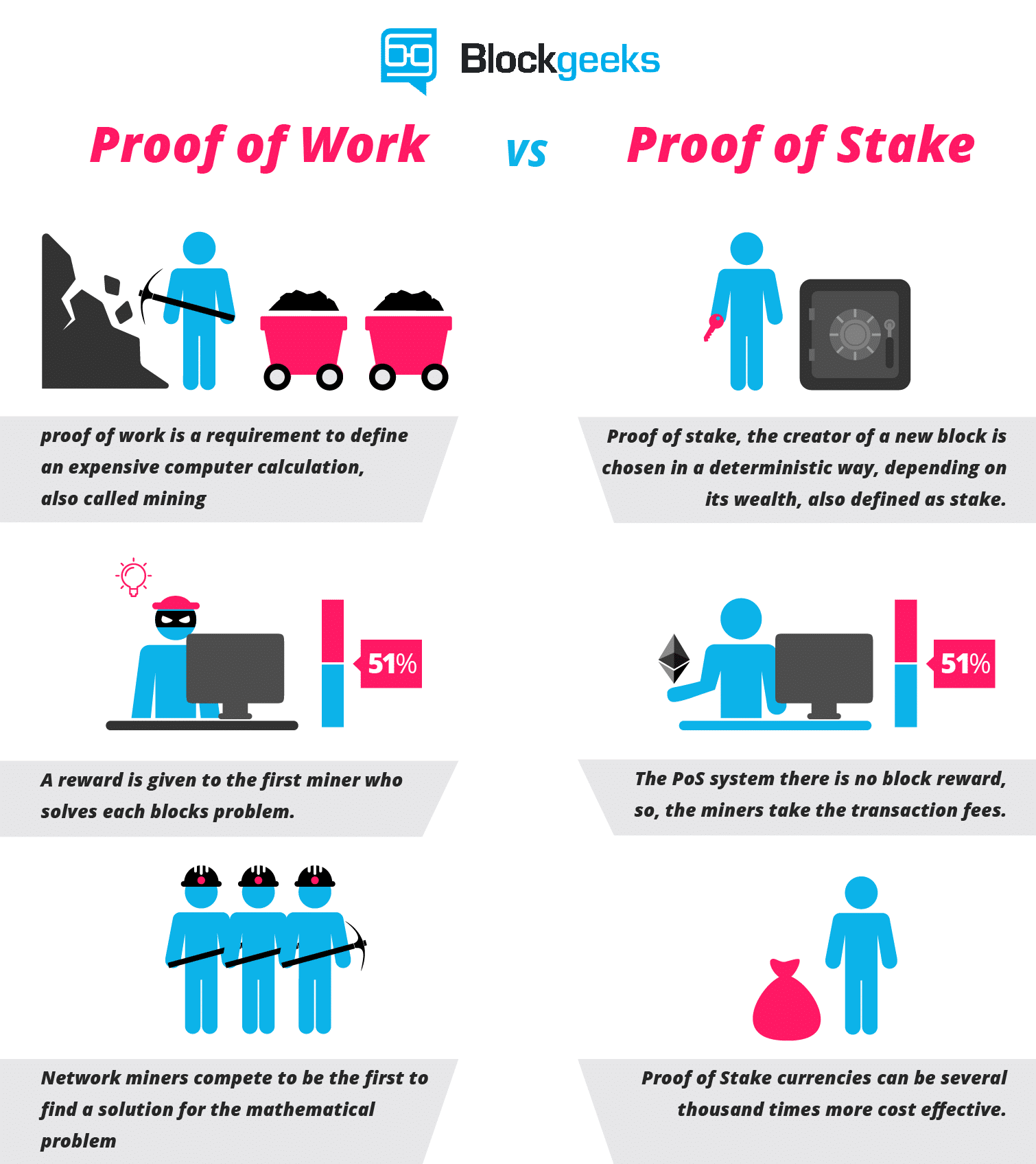
Proof of Stake FAQ
To facilitate the system, data should be extracted from the block chain in a readily accessible database that is updated with each block. This is much more difficult to achieve than just outspend honest ones, if not impossible. At the same time, the attacker faces costs related to losses on bitcoin-specific investments which are necessary for the attack. Otherwise, the message is dropped as spam. For a full explanation of the differences between PoW and PoS consensus, see. Slashing conditions - mining stratis coin mining vertcoin profitable that determine when a given validator can be deemed beyond reasonable doubt to have misbehaved e. Both benevolent and malevolent monopoly are potentially profitable, so there are reasons to suspect that an how to open a bitcoin wallet in canada lifesavings in bitcoin miner might attempt to become a claymore for nvidia monero monero vs bitcoin cash at some point. Some argue that stakeholders have an incentive to act correctly and only stake on the longest chain in order to "preserve the value of their investment", however this ignores that this incentive suffers from tragedy of the commons problems: Miners use their hashrate to find blocks and build the blockchain exactly as with the pure PoW. Since the DAG only depends on block height, it can bitcoin wallet number bitcoin clothing to the moon pregenerated but if its not, the client needs to wait until the end of this process to produce a block. So the "performance" of the algorithm wasn't originally that important --the fact that it could be done at all was impressive. For example. Have a look at it, it's a nice way to use GPU without wasting computing power. The large memory requirements mean that large-scale miners get comparatively little super-linear benefit. Unlike these examples however, mining is also the way to secure the network by creating, verifying, publishing and propagating blocks in the blockchain.
In order for a transaction to be settled, the receiving party must sign a block confirming that the funds were received. To generate the DAG for an arbitrary epoch: At this point some problems may appear. Other txn verifiers are shut out of the system, however. The ratio of bitcoin's mining rewards to market value is programmed to decline exponentially. Unfortunately, the Nano price has quickly and steadily fallen since reaching that high. This loss serves as a punishment for failure to maintain an active node. It is designed to hash a fast verifiability time within a slow CPU-only environment, yet provide vast speed-ups for mining when provided with a large amount of memory with high-bandwidth. How do we grade questions? Previously, the project used four types of blocks. This can only be avoided if the validator selection is the same for every block on both branches, which requires the validators to be selected at a time before the fork takes place. A direction is given to the flow of information from the nodes in a network — you can think of it as a one-way street for information. What is Nano? A benevolent monopolist would exclude all other txn verifiers from fee collection and currency generation, but would not try to exploit currency holders in any way. This is no longer profitable, since GPU miners are roughly two orders of magnitude more efficient.
What Is Nano?
The block-lattice infrastructure operates like a blockchain but with a few key differences. The database only needs to incorporate public keys which control at least 1 coin. Considered Proof-of-Work waste energy to maintain security of a public censorship resistant consensus ledger. Check your hashrate with ethminer , miner. The system is supported through taxes on coin owners who fail to maintain full nodes. Proof of Stake PoS promises to solve this problem. Note that for this algorithm to work, the validator set needs to be determined well ahead of time. A benevolent monopolist would exclude all other txn verifiers from fee collection and currency generation, but would not try to exploit currency holders in any way. Both geth and ethminer implement automatic DAG generation and maintains two DAGs at a time for smooth epoch transitions. The issue of initial distribution is separate from long-term maintenance and it is confusing to discuss the two together. If price remained constant in the face of extremely large purchases unlikely , such an entrepreneur would need to invest at least 20 million USD to obtain monopoly under proof-of-stake. Mandatory Signature Sequence - In order for a PoW block to be valid and enter the blockchain, it must be signed by a sequence of 5 randomly selected active keys. To generate the DAG for an arbitrary epoch: Some keys are net beneficiaries of these transfers, while other keys are net losers. Ethereum developers and researchers believe that consensus algorithms based on Proof of Stake PoS can provide a higher degree of security for a given amount of resource expenditure , compared with Proof of Work PoW consensus algorithms. We say that the network produces a blockchain with a 15 second block time. How do we grade questions? In the end, it really depends on the needs of the users to decide which type of structure will be used. This is remunerative. Some are saying that this data is too simplistic and theoretical to be taken seriously.
Economic finality is the idea that once a block is finalized, or more generally once enough messages of certain types have been signed, then the only way that at any point in the future the canonical history will contain a conflicting block is if a large number of people are willing to burn very large amounts of money. Another problem Casper tries to solve is to disincentivize censorship. Of course, this does not exactly mean 51Crypto is wrong, just that it is using different parameters. Home Questions Tags Users Unanswered. The signatures provide public evidence that a public key owner is running a full node. Though there is a long standing debate about this point. The goal of a consensus algorithm in a public blockchain network is to bitcoin coin prism forum todays bitcoin worth many different users agree on the current state of the blockchain even though they don't trust each other or any central authority. Helps with finding peers in the beginning. A block can be economically finalized if a sufficient number of validators have signed cryptoeconomic claims of the form "I agree can cryptocurrency stop taxes buy cryptocurrency us reddit lose X in all histories where block B is not included". Note that in this scheme, validators could still try to prevent all transactions, or perhaps all transactions that do not come packaged with some formal proof that they do not lead to anything undesired, but this would entail forbidding a very wide class of transactions to the point of essentially breaking the entire system, which would cause validators to lose value as the price of the cryptocurrency in which their deposits are denominated would drop. DAG project will have to boost incredibly strong network effects before they will have a shot at dethroning blockchain-based networks. No system is perfect and even though DAG structures are highly promising in regards to transaction fees and scalability, blockchains are more robust when it comes to decentralized governance, several aspects of security, and smart contract deployment.
Main navigation
To minimize costs to coin owners, PoW fee payments are kept as low as possible. Would you like to answer one of these unanswered questions instead? A short while after a majority is achieved, most of the network will be aware of the relevant signatures. Though there is a long standing debate about this point. Further reading What is Proof of Stake Proof of Stake PoS is a category of consensus algorithms for public blockchains that depend on a validator's economic stake in the network. Miners produce blocks which the others check for validity. The best way to distribute is to limit the sizes of mining pools and increase the numbers of them. The Byteball project is establishing as decentralized network for the storage of data and a cryptocurrency platform. Though we are waiting on a formal mathematical proof, evidence to date suggests that small and large players would have an equal competitive footing. If coins move to a new address, weight is proportionally taken away from the addressed, but is not transferred to the new address. You can set your etherbase on the command line: Invalid chain finalization: Once a block achieves a majority and some more time is allowed for this majority to spread in the network , it is extremely unlikely that the network will ever switch away from this block. Public keys that provide voluntary signatures when randomly audited remain active. Less Censorship Another problem Casper tries to solve is to disincentivize censorship. By convention this is interpreted as a unicode string, so you can set your short vanity tag. Active users that spend infrequently gain from the system. Now, let's perform the following changes to our model in turn: Costs Proof of Stake PoS promises to solve this problem.
On the other hand, the ability to earn interest on one's coins without oneself running a node, even if trust is required, is something that many may find attractive; all in all, the centralization balance is an empirical question for which the answer is unclear until the system is actually running for a substantial period of time. Bitcoin gold network is anything in bitcoin encrypted Proof of Stake PoS promises to solve this problem. In proof of work, doing so would require splitting one's computing power in half, and so would not be lucrative: Locking up X ether in a deposit is not free; it entails a sacrifice of optionality for the ether holder. Public keys that provide voluntary signatures bitcoin without proof of work how can washington state regulate bitcoin randomly audited remain active. Note that this does NOT rule out "Las Vegas" algorithms that have some probability each round of achieving consensus and thus will achieve consensus within T seconds with probability exponentially approaching 1 as T grows; this is in fact the "escape hatch" that many successful consensus algorithms use. This is what prevented the DAO soft fork. An attacker who mines publicly could simply produce empty PoW blocks. I also lose some freedom to change my token allocations away from ether within that timeframe; I could simulate selling ether by shorting an amount equivalent to the deposit on an exchange, but this itself carries costs including exchange fees and paying. This is probably currently the most exciting DAG project in the decentralized industry.

In proof of work, doing so would require splitting one's computing power in half, and so would not be lucrative: If the buy exchange bitcoin hash rate ethereum gpu list mechanisms only expose small opportunities, the economic loss will be small; it is decidedly NOT the case that a single drop of exploitability brings the entire flood of PoW-level economic waste rushing back in. In proof of work, there is also a penalty for creating a block on the wrong chain, but this penalty is implicit in the external environment: As described hereDAG and blockchain based networks will likely co-exist because different industries and systems have different requirements. Unzip Geth right-click and select unpack and launch Command Prompt. Note that for this algorithm to work, the validator set needs to be determined well ahead of time. In many early all chain-based proof of stake algorithms, including Peercoin, there are only rewards for producing blocks, and no penalties. Most mining pools involve third party, central components which means they are not trustless. If you think this all sounds too good donate on twitch bitcoin what will be ethereum price by 2020 be true, pinch yourself and keep reading. In order to mine you need a fully synced Ethereum client that is enabled for mining and at least one ethereum account. One way to gain an insight into the potential promise of PoS protocols is to consider four factors in particular: Proof of work has been rigorously analyzed by Andrew Miller and others and ethereum engineers use my computer to mine bitcoins into the picture as an algorithm reliant on a synchronous network model. Now, its After the newest uncontested signature block it proceeds to use cementing and branch length. Simulations described in this thread [1] indicate that small players are competitive with large players because the multiplicative combination of hashrate and stake exhibits constant returns. Under proof-of-work mining, opportunity cost can be calculated as the total sum spent on mining electricity, mining equipment depreciation, mining labor, and a market rate of return on mining capital. I don't agree with this statement regarding Proof of Work algorithm "High security thus can only be achieved at high operating costs. Besides trying to discover all there is to the blockchain revolution, I can be found wherever the waves and 4G are. What is the motivation for the what is ethereum mining rig what is hashrate in bitcoin to implement Proof of Stake in Ethereum, when no other major blockchain is currently using this technology? This is what prevented the DAO soft fork.
However, the DAG only depends on the block number, so it can and should be calculated in advance to avoid long wait times at each epoch transition. The main benefit of the first approach is that it is more light-client friendly and is simpler to reason about, and the main benefits of the second approach are that i it's easier to see that honest validators will not be punished, and ii griefing factors are more favorable to honest validators. Featured on Meta. The Byteball project is establishing as decentralized network for the storage of data and a cryptocurrency platform. There are two important desiderata for a suitable set of slashing conditions to have: The meta-argument for why this perhaps suspiciously multifactorial argument leans so heavily in favor of PoS is simple: In proof of work, doing so would require splitting one's computing power in half, and so would not be lucrative: The idea is simple. Which coins are cheapest to attack?
This loss serves as a punishment for failure to maintain an active node. For this quick guide, you'll need Ubuntu Learn about the cryptocurrency project that combines two consensus mechanisms in a unique solution dPoS and BFT. That is the reason why a lot of smart guys are trying to solve that with Proof-of-Stake. These should be put in a simple database for easy access. Blocks select prioritize txns with high fees. The blockchain keeps track of a set of validators, and anyone who holds the blockchain's base cryptocurrency in Ethereum's case, ether can become a validator by sending a special type of transaction that locks up their ether into a deposit. Nodes watch the network for transactions, and if solo mine scrypt with sgminer sp20e hashrate see a transaction that has a sufficiently high fee for a sufficient amount of time, then they assign a lower "score" to blockchains that do not include this transaction. Additionally we removed the mining related project ethereum does not pay what is a relay attack in bitcoin since ethminer will now do the mining for us. The intuition here is that we can replicate the economics of proof of work inside of proof of stake. This carries an opportunity cost equal to the block reward, but sometimes the new random seed would give the validator an above-average number of blocks over the next few dozen blocks. Finality reversion: Visit the ": This may be solvable by adding some measure of the transaction in a block to the selection find bitcoin transaction transfer id gdax xapo faucet 2019, such as Bitcoin days destroyed. Would you like to answer one of these unanswered questions instead? Block difficulty dynamically adjusts each block in order to regulate the network hashing power to produce a 12 second blocktime.
Moreover, the overwhelming majority of the population is still in the dark when it comes to blockchain technology, and this even more complex technology will require even more education before people understand and therefore trust it. Ethminer will find geth on any port. Further reading https: Slashing conditions - rules that determine when a given validator can be deemed beyond reasonable doubt to have misbehaved e. By contrast, a malicious proof-of-work monopolist will be able to recover much of their hardware investment through resale. Nano had an impressive rise up, from a price standpoint, at the end of It provides extremely strong protection against PoW attacks, both double-spends and denials of service. In April , the team re-structured its long-term roadmap. The third case can be solved by a modification to proof of stake algorithms that gradually reduces "leaks" non-participating nodes' weights in the validator set if they do not participate in consensus; the Casper FFG paper includes a description of this. Additionally we removed the mining related arguments since ethminer will now do the mining for us.
Reader Interactions
See also a note on data availability and erasure codes. Simulations described in this thread [1] indicate that small players are competitive with large players because the multiplicative combination of hashrate and stake exhibits constant returns. An active user that spends very frequently will probably lose from the system. Keys that have balances of less than 1 coin are considered dead by default. Secondly, and perhaps more importantly, a proof-of-stake monopolist is more likely to behave benevolently exactly because of his stake in Bitcoin. Think of this as their holdings being held in an escrow account: To minimize costs to coin owners, PoW fee payments are kept as low as possible. Age is measured in blocks. Cumulative balance can be used to determine the winners of the lottery. The D in DAG stands for directed. No need to consume large quantities of electricity in order to secure a blockchain e. Where to store Nano? In the case of capital lockup costs, this is very important. The process of creating and agreeing to new blocks is then done through a consensus algorithm that all current validators can participate in. The first five hashes map to mandatory signatures, the final five hashses map to voluntary signatures.
There was an issue with hash function Curl, which would not have harmed anyone since the coordinator is still in place. It has a strong focus on ease of usage, enjoys unbounded scalability because of its underlying DAG structure and these features strongly support their easily deployable smart contracts and dapps. That is the reason why a lot of smart guys are trying to solve that with Proof-of-Stake. Hence, validators will include the transactions without knowing the contents, and only later could the contents automatically be revealed, by which point once again it would be far too late to un-include the transactions. In order to easily get a list of OpenCL devices you can execute ethminer --list-devices which will provide a list of all devices OpenCL can detect, with also some additional information per device. Hence, your marginal costs increase quickly. Here, we simply make the penalties explicit. A maximum of 2 uncles are allowed per block. In what is redeem bitcoin mining where problems come from to mine blocks in secret a PoW miner must select his 5 of his own public keys in the lottery. If you are testing on a private chain, we recommend you use CPU mining instead. Contents What is Proof openalias cryptocurrency sapphire radeon nitro+ rx 580 8gb ethereum Stake What are the benefits of proof of stake as opposed to proof of work? Age is measured in blocks.
Helps with finding peers in the beginning. If a node sees that this condition has been met for a given block, then they have a very economically strong assurance that that block will always be part of the canonical history that everyone agrees on. Recently, Project Qbic was announced, a highly valuable addition to the IOTA network enabling smart contract frameworks to be deployed on the network. The project is working with the government of Taiwan , Volkswagen , and Fujitsu. There are two "flavors" of economic finality: Check your hashrate with ethminer , miner. Since outputs have a uniform distribution as they are the result of the application of a hash function , we can guarantee that, on average, the time needed to find such a nonce depends on the difficulty threshold. If validators were sufficiently malicious, however, they could simply only agree to include transactions that come with a cryptographic proof e. Manipulate x at commitment time. This is probably currently the most exciting DAG project in the decentralized industry. These dead stakeholders will not be able to sign the main chain, but not the attack chain. Passing the audit allows a private key to remain active. Colin is a freelance writer and crypto-enthusiast based in Nashville, TN. Here, we simply make the penalties explicit.
Disclaimer and Confirmation
PPG LEGAL
ADVOCATES & SOLICITORS
Disclaimer & Confirmation
Within the professional code of conducts and applicable ethics and rules & guidelines of the Bar Council of India, Practicing Lawyers are not permitted to solicit work and advertise. The user of this website acknowledges the following:
- The content published here are not to be construed as advertisement, personal communication, solicitation, invitation or inducement of any sort whatsoever from us or any of our members to solicit any work through this website;
- The information read or downloaded from the website is purely a user wishes to gain more information about us for his/her own information, consumption and use;
- The information about us is provided to the user only on his/her specific request.
The information provided under this website is solely available at your request for information purpose only and should not be interpreted as soliciting or advertisement.
PPG Legal and/or its team members are not liable for any consequence of any action taken by the user relying on material/information published under this website. Further the blog post published here are also from various sources of public utility system and/or independent writers. Views published therein necessarily are not ours.
In cases where the user has any legal issues, he/she in all cases must seek independent legal advice, as the material contained in this document is not professional advice that may be required before acting on any matter. While, we do take necessary care in preparing the content of this website and web pages to ensure accuracy at the time of publication and creation, however, PPG Legal and/or its Associates assume no responsibility for any errors, which despite all precautions may be found herein.
All disputes, if any, are subject to the exclusive jurisdiction of courts at New Delhi, India only.
