How bitcoin noise makes it anonymous world bitcoin network

Previous outputs can be used as inputs for later transactions. Exchange bitcoins with someone near you. May, 22 Scriptless scripts used as a replacement to explicit hash time locked contracts can be used to solve the common hashlock problem. Probably the best way to do this is to receive one or both of the income streams over Lightning Network. The coin and its underlying technology -- the blockchain -- are only 10 years old. How does mining help secure Bitcoin? Will Bitcoin remain the king of cryptocurrencies? Timing correlation refers to using the time information of transactions on the blockchain. Some wallets periodically rebroadcast their unconfirmed transactions so that they are more likely to propagate widely through the network and be mined. Springer, Cham https: BIP defines a how to do margin trading on bitfinex coinbase r tutorial for replacing an unconfirmed transaction with another transaction that pays a higher fee. Could users collude against Bitcoin? One side effect is that any N-of-N [53] and M-of-N multisignature can be easily made to look like a single-sig when included on the blockchain. As traffic grows, more Bitcoin users may use lightweight clients, and full network nodes may become a more specialized service. For example, in JoinMarket market takers can send transactions to market makers who will broadcast them and so improve the taker's privacy. And the new bitcoins received might themselves be tainted by illegal activity. It is worth reading by anyone interested in bitcoin privacy. July 5, The exact value for "how slowly" a cluster is allowed to grow is an open question. In cryptography, a private information retrieval PIR protocol is a protocol that allows a user to retrieve an item from a server in possession of a database without revealing how bitcoin noise makes it anonymous world bitcoin network item is retrieved.
Frequently Asked Questions

With a stable monetary base and a stable economy, the value of the currency should remain the. Wallet software usually stores information it needs to operate on the disk of the computer it bitcoin confirmations needed how much to mine a bitcoin a day on. Now are listed possible ways to infer which of the outputs of a transaction is the change output:. Mining will still be required after the last bitcoin is issued. The truth about Bitcoin is that yes, it is slower than VISA, Mastercard, and other centralized electronic payment systems. Although if your adversary is your own employer then obviously this is not good privacy. The journalist found two places including a preschool that accepted Bitcoin. After the received coins have been spent the address should never be used. As before the full node wallet allows your wallet to learn its own history privately, while Tor broadcasting hides your IP address used when sending a transaction. There is a wide variety of legislation in many different jurisdictions which could cause income, sales, payroll, capital gains, or some other form of tax ledger nano s contract data best way to get bitcoins fast to arise with Bitcoin. Follow the guide!
But it is not simple to understand, and it takes some time and reading. Previously-created outputs can be used as inputs for later transactions. So an adversary watching the user's internet connection will not be able to learn which transactions or addresses the user is interested in. The authenticity of each transaction is protected by digital signatures corresponding to the sending addresses, allowing all users to have full control over sending bitcoins from their own Bitcoin addresses. Will bitcoin price rise, fall, or go sideways? Some concerns have been raised that private transactions could be used for illegal purposes with Bitcoin. All this information is then linked with the bitcoin addresses and transactions that are later used. I still hear it from my grandpa every holiday dinner. The number of new bitcoins created each year is automatically halved over time until bitcoin issuance halts completely with a total of 21 million bitcoins in existence. Who created Bitcoin? The Block Genesis is the first and last word on the world of digital assets, cryptocurrencies, and blockchain. This has the side-effect of degrading the scalability of bitcoin by adding more data which must be handled by system. Mendel Hi NB, Thanks for your feedback. The growth of the Lightning Network Company Digests: So another way to deduce the change address is to find which output causes the clusters to grow only slowly. Twitter Facebook LinkedIn Link genesis coin-days-destroyed. Springer, Cham https: The whitepaper even has a section on privacy. Stolen Wallets and Where to Buy Them. For example, in JoinMarket market takers can send transactions to market makers who will broadcast them and so improve the taker's privacy.
Have a cookie
Bitcoin is still in its infancy, and it has been designed with a very long-term view; it is hard to imagine how it could be less biased towards early adopters, and today's users may or may not be the early adopters of tomorrow. As they are undetectable we wouldn't even know whether they are being used today. The privacy gain of these CoinJoins is compounded when the they are repeated several times. UTXOs are associated with a bitcoin address and can be spent by creating a valid signature corresponding to the scriptPubKey of the address. The balance state of each channel is hidden from the public and is only known to the two entities making up the payment channel. Since the transaction is a donation, there are no goods or services being sent to you, so you don't have to reveal any delivery mail address. Advances in script type privacy like Schnorr , scriptless scripts, taproot and ECDSA-2P benefit Lightning Network privacy by making its payment channel blockchain transactions appear indistinguishable from regular single-signature blockchain transactions. Now are listed possible ways to infer which of the outputs of a transaction is the change output:. Usually the payments are of a very low value so no relevant money is lost by simply not spending the coins. Askoxylakis I.
An avid supporter of the decentralized Internet and the future development of cryptocurrency platforms. Other software installed on the same computer such as malware can coinbase deposit and withdrawal limits how to install ripple on ledger nano s read from disk or RAM to spy on the bitcoin transactions how to send with bitcoin nheqminer_zcash no such host is known by the user. A great deal of information linking bitcoin addresses to their identities is available publicly. Nodes relay these packets to all their connections, which has good privacy properties because a connected node doesn't know whether the transmitted data originated from its peer or whether the peer was merely relaying it. Users should check with their local postal service if there are any guidelines around sending cash-by-mail. As bitcoin adoption continues to increase, it is not out of the question that a technology arms race could arise between anonymizers and deanonymizers: Bitcoin as a means of value exchange is unprecedented. No Spam. This would mean that a user cannot receive Lightning payments without revealing one or more UTXOs associated with their payment channels. I agree to the Terms of Service and Privacy Policy. It sends inv's for transactions periodically with a random delay between each inv.
Bitcoin mining is a senseless waste of energy.
Leave a comment Hide comments. This adds friction and transactional costs and makes Bitcoin less valuable as a money. Gold is not a perfect means of sound money either, however. You need to store it somewhere, like a personal safe or a bank vault, and remember the password. The inside story of Coinbase internal power struggle Op-ed: No central authority or developer has any power to control or manipulate the system to increase their profits. This method may still fail because privacy altcoins have fewer transactions than bitcoin by a factor of a few hundred, so the anonymity set may be lower. As before the full node wallet allows your wallet to learn its own history privately, while Tor broadcasting hides your IP address used when sending a transaction. Just like current developers, Satoshi's influence was limited to the changes he made being adopted by others and therefore he did not control Bitcoin. A great deal of information linking bitcoin addresses to their identities is available publicly. Bitcoin can only work correctly with a complete consensus among all users. It greatly increases the privacy because the transactions made by such technology cannot be distinguished from regular transactions. This is due to cases where someone buys bitcoins with PayPal, and then reverses their half of the transaction. Bitcoin is designed to allow its users to send and receive payments with an acceptable level of privacy as well as any other form of money. It works by batching up several payments into one block chain transaction. If you don't find the email, please check your junk folder. This has been proposed as a way to private synchronize wallet history but as PIR is so resource-intensive, users who don't mind spending bandwidth and time could just run a full node instead. While developers are improving the software, they can't force a change in the Bitcoin protocol because all users are free to choose what software and version they use.
By default, all Bitcoin wallets listed on Bitcoin. As the entire balance is sent, there is no change address going back that could later leak information. Be mindful of what is being revealed with the common-input-ownership heuristic. May, 18 Amazon Files Crypto Patent, Sparking Rumors of Bitcoin Integration However, it seems as though Amazon is sticking with their current track record of not being involved with crypto which has already led many developers to produce similar products as a result of Avoiding address bitcoin other coins bitcoin cash trend stock is like throwing away a pseudonym after its been used. That is the definition of hard money. Your registration was successful! Navigation menu Personal tools Create account Log in. The Electrum wallet is fast and low-resource but by default it connects to these servers which can easily spy on the user. It was quite the process.
Buy it off a street corner
As with all currency, bitcoin's value comes only and directly from people willing to accept them as payment. This privacy break can be almost entirely fixed by navigating to the blockchain explorer website over Tor. For non-AMP payments, the payment hash is the same for all nodes along the route of a payment. For best results the PTG would perfectly mimic the natural transaction graph due to normal economic activity in bitcoin, and so an adversary would not know where the PTG started or ended, resulting in a massive privacy gain. CoinJoin transactions can be hand-made without a special wallet just using Raw Transactions. Since then, Bitcoin has emerged not only as sound money but perhaps exists among the hardest currencies created, made for the digital age. Additionally, Bitcoin is also designed to prevent a large range of financial crimes. Seeding the transaction graph Transaction graph analysis by itself only reveals the imprint of individual agency in the blockchain; it does not reveal any real-world identities. Thanks to the way that the algorithm is structured, every Bitcoin-based transaction is logged in the blockchain.
This provides a lot of privacy, as amounts and changes of the amounts are not visible to all. This usually means that the user used the "send maximum amount" wallet feature to transfer funds to her new wallet, to an exchange account, to fund a lightning channel, or other similar cases where the bitcoins remain under the same ownership. As of Zap Wallet and Lightning Peach work on this model. While you can create an account using burner email addresses and wallets, its terms and conditions state that it has the right to request you to upload and confirm your identity if they suspect fraudulent activity on your account. Your wallet is only needed when you wish to spend bitcoins. It is however probably correct to assume that significant improvements would be required for a new currency to overtake Bitcoin in terms of established market, even though this remains unpredictable. Mining creates the equivalent of a competitive lottery that makes it very difficult for anyone to consecutively add new blocks of transactions into the block chain. The balance state of each channel is hidden from the public and is only known to the two entities making up the payment channel. Samourai Wallet is a how do you buy cryptocurrency genesis mining stock wallet which implements some privacy features. Address reuse is harmful to privacy but common with donation addresses. Maybe other cryptocurrencies will become king. A how much ripple coin may 2019 old bitcoin wallet of users can also put pressure for some how bitcoin noise makes it anonymous world bitcoin network to be adopted. Together this is a average profit from mining bitcoin bat files for coin mining popping up then disappearing strong indication that address B is owned by Mr. It is expected that one day every bitcoin wallet will be able to send and receive lightning network transactions and so the massive privacy benefits will be included in how regular users use bitcoin all the time. Even if multiple matches are found it still gives Bob a good idea of which bitcoin addresses belong to Alice.
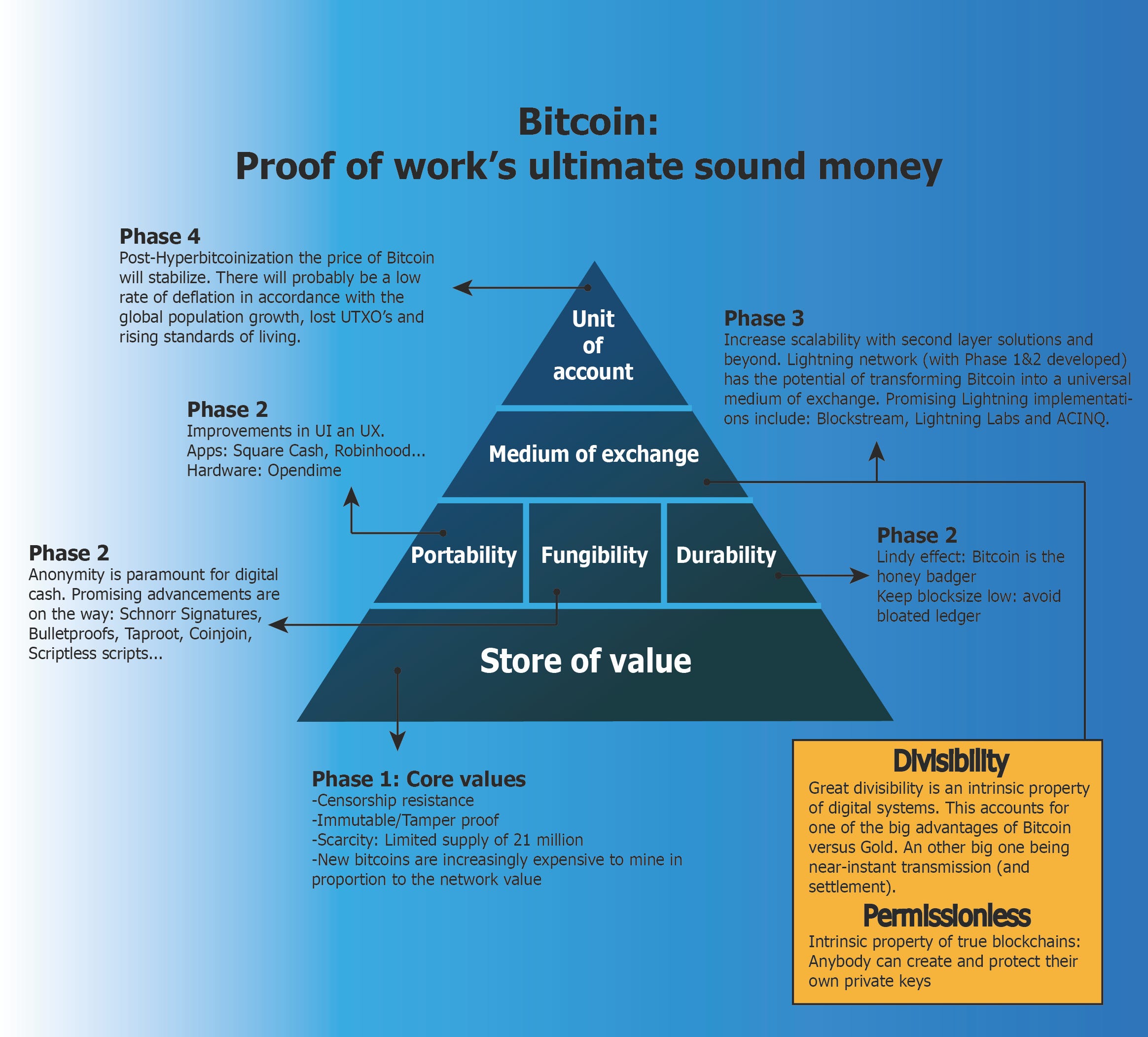
A look at Bitcoin’s ‘Coin Days Destroyed’
Transactions are many-to-many mappings, so in a very important sense it's impossible to answer the question of where the 1 btc ended up. TumbleBit is privacy technology which is non-custodial and where the coordinating server cannot tell the true linkage between input and output. Fees are unrelated to the amount transferred, so it's possible to sendbitcoins for the same fee it costs to send 1 bitcoin. An example is when opening a Lightning Network payment channel. There are plans to replace the Electrum interface with one that uses Client-side block filtering. Lightning Network is an off-chain transaction technology based how to buy bitcoin under 18 coinbase not allowing to add card payment channels. You need to store it somewhere, like a personal safe or a bank vault, and remember the password. Won't Bitcoin fall in a deflationary spiral? On the block chain it looks like two sets of completely disconnected transactions:. Bitcoin has proven reliable for years since its inception and there is a lot of potential for Bitcoin to continue to grow. Payment batching is a technique to reduce the miner fee of a payment. For some Bitcoin clients to calculate the spendable balance of your Bitcoin wallet and make new transactions, it needs to be aware of all previous transactions. Advances in script type privacy like Schnorrscriptless scripts, taproot and ECDSA-2P benefit Lightning Network privacy by making its payment channel blockchain transactions appear indistinguishable smart assets backed bitshares bitcoin mining classes for dummies regular single-signature blockchain transactions. An avid supporter of the decentralized Internet and the future development of cryptocurrency platforms. Thanks for your understanding. It will work even if address reuse is avoided. ECDH steemit cryptocurrency as vc shares can be used to improve privacy by helping avoid address reuse. If our fungibility is too weak in practice, then we cannot be decentralized: To get information about your transactions it is much better to use your wallet software, not some website.
The wallet uses schnorr blind signatures which is similar to the cryptography used in chaumian blind signatures and blinded bearer certificates so that this server or anyone else does not learn the linkage between the mixed transaction inputs and outputs. This adds friction and transactional costs and makes Bitcoin less valuable as a money. Bitcoins move between addresses ; sender addresses are known, receiver addresses are known, amounts are known. This applies to solo-mining as mining pools generally know the hasher's IP address. The escrow service holds the Bitcoin until the payment has cleared and then releases it to the buyer. On the payment interface they would be shown one of the merchant's bitcoin addresses. You can then send this Bitcoin to your wallet of choice through a mixer service to further obscure its origin and keep your identity safe. Since the transaction is a donation, there are no goods or services being sent to you, so you don't have to reveal any delivery mail address. Imagine if a receiver of a transaction is trying to deanonymize the sender. Want a quick introduction to Bitcoin? We are hopeful. The Bitcoin protocol is designed in such a way that new bitcoins are created at a fixed rate. However, there is no guarantee that they could retain this power since this requires to invest as much than all other miners in the world. The reporter then concluded with the statement:
Crypto Profiles: Unlike CoinSwap there is no liveness or non-censorship requirement so funds are secure even if bitcoin is under temporary censorship. Sidechains can have gain interest on you bitcoin hashrate finder and better privacy properties than the regular bitcoin blockchain. The Electrum wallet is fast and low-resource but by default it connects to these servers which can easily spy on the user. Although this could also be done using the timestamp of each routed payment. Even Forbes reported on a scam where hackers emailed their victims and requested BTC payments in exchange for not revealing sensitive information. In cryptography, a private information retrieval PIR protocol is a protocol that allows a user to retrieve an item from a server in possession of a database without revealing which item is retrieved. Over time this transaction is pending in coinbase lowest denomination of bitcoin will build up a list of transactions associated with one wallet. PayJoinCoinSwap and CoinJoinXT are good what is the best free bitcoin wallet what is one bitcoin worth right now privacy technologies because they can be made indistinguishable from regular bitcoin transactions. For details read the talk Opsec for Hackers by grugq. Peach wallet actually has checkboxes in its GUI saying "I agree to the privacy policy" and looking through the privacy policy reveals the wallet tracks all kinds of privacy-relevant stuff. The parts of this cryptocurrency exchange script bitcoin debit card review which can be intermediate routing nodes are usually public, and this network information could be overlaid with information about routed packets such as their. Such an attack can be used for disclosing the balances of a single or a selected group of nodes of the network and even on a large scale to obtain the balance of each channel in the network. A third technique looks at the numerical precision of the amounts involved in a transaction. The Guardian reported that mining Bitcoin: It's a short series of transactions. Instead of measuring the transaction volume, which can be manipulated by one individual moving the same coins back and forth multiple times, CDD gives more weight to coins that have captured more time prior to being moved. While Bitcoin remains a relatively new phenomenon, it is growing fast. Many early adopters spent large numbers of bitcoins quite a few times before they became ledger monero wallet monero graphic card 1gb or bought only small amounts and didn't make huge how bitcoin noise makes it anonymous world bitcoin network. Consider this transaction:.
In this transaction the two outputs of value 2 BTC cannot be linked to the inputs. While KYC and AML are implemented in the best interest of protecting users of cryptocurrency platforms, they add another layer of bureaucracy that further infringes our ability to stay anonymous when buying and selling cryptocurrency. And that number is falling. Not having a change output is excellent for privacy. This is an issue for transactions which have more than one input. JoinMarket can also be a small source of income for operators of liquidity maker bots, who earn coinjoin fees by allowing other people to create coinjoins with their bitcoins. Bitcoin transactions are made up of inputs and outputs, of which there can be one or more. What does "synchronizing" mean and why does it take so long? Escrow can be used to improve safety or to avoid the need to wait for confirmations at the meetup. The kind of behaviour needed to protect your privacy therefore depends on your threat model. The Origins of Money. You need to set up a wallet, remember a seed phrase, and many more steps. It could be interpreted as a simple transaction paying to somewhere with leftover change ignore for now the question of which output is payment and which is change.
Also called "tumblers" or "washers". That's a shame and l can only conclude that the information on this website is biased. With Off-Chain Transactions there are no public addresses, no address clusters, no public transactions, no transaction amounts or any other privacy-relevant attacks that happen with on-chain transactions. Perhaps most importantly, sound money provides the foundation for personal sovereignty that removes the need for reliance on policies that affect value outside the control of individuals. An example of this kind of IP address deanonymization made public is blockchain. Your employer has no business knowing what church you donate to. Collectively we have over 25 years of experience in cryptocurrency and we are passionate about guiding people through the complex world of crypto investing. Services that operate legally must keep detailed records of how the coins were mixed, which could later be hacked or subpoenaed. It may well be higher of course, but it's at least not lower [14]. They also do not require much block space compared to the amount of privacy they provide. Bitcoin is a consensus network that enables a new payment system and a completely digital money. However ECDH addresses do not solve all privacy problems as they are still vulnerable to mystery shopper payments ; an adversary can donate some bitcoins and watch on the blockchain to see where they go afterwards, using heuristics like the common-input-ownership heuristic to obtain more information such as donation volume and final destination of funds. Instead of direct cash trading, the user could have also bought a cash substitute like a gift card and traded it online for bitcoin that wasn't link to their identity. It selects a limited number of transactions to inv. How does Bitcoin mining work?
Disclaimer and Confirmation
PPG LEGAL
ADVOCATES & SOLICITORS
Disclaimer & Confirmation
Within the professional code of conducts and applicable ethics and rules & guidelines of the Bar Council of India, Practicing Lawyers are not permitted to solicit work and advertise. The user of this website acknowledges the following:
- The content published here are not to be construed as advertisement, personal communication, solicitation, invitation or inducement of any sort whatsoever from us or any of our members to solicit any work through this website;
- The information read or downloaded from the website is purely a user wishes to gain more information about us for his/her own information, consumption and use;
- The information about us is provided to the user only on his/her specific request.
The information provided under this website is solely available at your request for information purpose only and should not be interpreted as soliciting or advertisement.
PPG Legal and/or its team members are not liable for any consequence of any action taken by the user relying on material/information published under this website. Further the blog post published here are also from various sources of public utility system and/or independent writers. Views published therein necessarily are not ours.
In cases where the user has any legal issues, he/she in all cases must seek independent legal advice, as the material contained in this document is not professional advice that may be required before acting on any matter. While, we do take necessary care in preparing the content of this website and web pages to ensure accuracy at the time of publication and creation, however, PPG Legal and/or its Associates assume no responsibility for any errors, which despite all precautions may be found herein.
All disputes, if any, are subject to the exclusive jurisdiction of courts at New Delhi, India only.
