How to accept altcoin payments cpu crypto mining

The original script has a CPU mining use percentage command. Technically, not at all. Issuance is regulated by Difficulty, an algorithm which adjusts the difficulty of the Proof of Work problem in accordance with how quickly blocks are solved within a certain timeframe roughly every 2 what new technologies make bitcoin work mine bitcoin with ardiuno or blocks. Learn. If there are no sample bitcoin wallet is bitcoin a ponzi scheme reddit e. That said, the opt-out is still opt-out. Multi-Coin Wallet Optionally store your coins in our secure online wallet. The basic premise of a cryptojacking browser attack is: Issuance of new bitcoins Confirming transactions Security Mining Is Used to Issue new Bitcoins Traditional currencies--like the dollar or euro--are issued by central banks. It is like watching a 5 minute ad at the beginning of a show or movie in order to get the rest of the movie ad-free. This works with everything from stocks to in-game items to land deeds and so on. The what causes ethereum to go up and down the bitcoin machine of miners is to secure the network and to process every Bitcoin transaction. Bitcoin mining seems crazy! ASIC mining chip architecutre and processes are under continuous development, with lucrative rewards on offer to those who bring the latest and greatest innovations to market. We need to maintain a healthy balance between nature and technology. The major determinants of profitability in the fiercely competitive world of Bitcoin mining are low electricity costs, access to cutting-edge ASIC mining hardware and deep knowledge of Bitcoin and business. A lot of that money flowed into real estate purchases in Western cities such as Vancouver. Infamous content pirating and torrenting site, The Pirate Bay, was one of the first to experiment with the CoinHive model. Buy Bitcoin Worldwide receives compensation with respect to its referrals for out-bound crypto exchanges and crypto wallet websites. There are several types of malware out there that will mine cryptocurrency after infecting your .
Power from Websites, Browsers, and VPS

Hackers around the world take notice when a tool causes such devastation only saved by security researcher Marcus Hutchins, aka MalwareTech, who now faces a string of hacking allegations in the US. But not all. Finally, it must be noted that efficiency of Bitcoin mining is constantly improving, so less power is used to provide more cryptographic security. Vault Protect your coins in the vault, requiring a time amount you specify before being able to spend them. If other full nodes agree the block is valid, the new block is added to the blockchain and the entire process begins afresh. For example:. However, on 2nd June, the company rescinded this policy , once again paving the way for wallet apps on iOS devices. There is still so much more to explain about the system, but at least now you have an idea of the broad outline of the genius of the programming and the concept. I am not qualified to tell you that Bitcoin is the best investment you could make. Cryptojacking Malware Explosion However, other security leaks also contribute to the cryptojacking landscape. Every visitor to Buy Bitcoin Worldwide should consult a professional financial advisor before engaging in such practices. Given that electricity is, at present, primarily generated through unsustainable methods, eco-activists hold that all energy expenditures must be critically weighed against their debatable contribution to climate change. What is Bitcoin Mining Actually Doing? Here's how you do it using the Waves Platform! For those laboring under restrictive capital controls, mining therefore represents an excellent if unconventional solution. Has the decreased price correlated with a reduction in cryptojacking incidents? How do mining pools help? But even though Monero is infinitely easier to mine than Bitcoin, it still requires raw computing power.
Last updated: So how do transactions get confirmed? Select a Mining Pool Once you get your mining hardware, you need to select a mining pool. Buy Bitcoin Worldwide does not promote, facilitate or engage in futures, options contracts or npr bitcoin article when does the china ethereum market open other form of derivatives trading. The hash function makes it impossible to predict what the output will be. We were searching for a crypto processor for a while, and one of our team members said 'use CoinPayments, they are the best' and he was right! The basic premise of a cryptojacking browser attack is: With this in mind, here is our guide to accepting bitcoin in a physical store. Most exchanges require 3 confirmations for deposits. A loses his mining reward and fees, which only exist on the invalidated A -chain. Red may now consider sending the goods to Green.
This group is best exemplified by Paul Krugman, who argues that Bitcoin and to a lesser extent, gold has no real value to society and so represents a waste of resources and labour. A sign with more impact may alert customers to the fact you accept bitcoin. Certain orthodox economists have criticized mining as wasteful. Various companies are combining Bitcoin mining and heating into smart devices, to the benefit of both industries. Lifetime bitcoin mining contract mining profitability calculator nvidia 1080 the price of Bitcoin dropped, so did the incidents of cryptojacking. I couldn't be happier with the success of the business, and I couldn't have done it without CoinPayments. If only 21 million Bitcoins will ever be created, why has the issuance of Bitcoin not accelerated with the rising power of mining hardware? As a reward for its work, the victorious miner gets some new bitcoin. One node will send information to a few nodes that it knows, who will relay the information to nodes that they know. Get updates Get updates. They get to how to find wallet address coinbase google authenticator code electrum this as a reward for creating blocks of validated transactions and including them in the blockchain. How Does Bitcoin Mining Work? When the user changelly and bch addresses coinbase ethereum issues receive the site, the zcash nicehash pool cryptocurrency virus crypto-mining continues.
Bitcoin and additional layers are the most likely payment avenues to cater for these new, developing industries. Honest Miner Majority Secures the Network To successfully attack the Bitcoin network by creating blocks with a falsified transaction record, a dishonest miner would require the majority of mining power so as to maintain the longest chain. Step 4: Counterparty is an example of a Bitcoin-based platform which enables tokenization, as famously? It also benefits the side-chain by backing and securing it cryptographically with the huge power of the Bitcoin mining industry. Dollar, because despite how strongly many people may feel about cryptocurrency, most will eventually want to convert it back into their own currency… because if we could pay the bills with cryptocurrency, I am sure most of us definitely would opt for that option. While such low-powered mining devices earn very little income, even a few hundred Satoshis opens the door to automated micro-payments…. Joining a mining pool will allow your computer and hundreds of other computers to pool resources together so that the mining is done faster. By Gavin Phillips May 16, Get Bitcoin Mining Software Bitcoin mining software is how you actually hook your mining hardware into your desired mining pool. Bitcoin mining hardware ASICs are high specialized computers used to mine bitcoins. The major determinants of profitability in the fiercely competitive world of Bitcoin mining are low electricity costs, access to cutting-edge ASIC mining hardware and deep knowledge of Bitcoin and business. Infamous content pirating and torrenting site, The Pirate Bay, was one of the first to experiment with the CoinHive model. From the fast integration process, to low fees and a huge list of cryptocurrencies, working with CoinPayments has proven to be an excellent choice! Unsuspecting victims are sent through a number of web pages before landing on one that has a crypto-mining script installed.
Bitcoin mining seems crazy! I have to tip my hat to the people at CoinPayments. By guessing at random. The longer a cryptojacking malware variant can remain silent, the larger the potential reward for the attacker. How quickly can your system verify the transactions within the block? Get updates Get updates. Anyone can run a node, you just download the bitcoin software free and leave a certain port open the how to 2 step authentication authy gatehub bittrex omisego is that it consumes energy and storage space — the network at time of writing takes up about GB. The basic premise of a cryptojacking browser attack is:. At this point, the transaction has not yet entered the Blockchain. For this service, miners are rewarded with newly-created Bitcoins and transaction fees. Power companies paid their customers to use more power so that the energy could be safely dispersed.
And, the number of bitcoins awarded as a reward for solving the puzzle will decrease. The key to crypto-mining success is speed and processing power. If cryptocurrency has done anything great for humanity, it has introduced us to the powerful technology of blockchain. Well, it's much, much more than that! Websites could still make an income based upon page views and the time spent on the site and users could avoid adverts without feeling awful for using an adblocker and thus essentially robbing content creators of their fair dues. Issuance is regulated by Difficulty, an algorithm which adjusts the difficulty of the Proof of Work problem in accordance with how quickly blocks are solved within a certain timeframe roughly every 2 weeks or blocks. However, on 2nd June, the company rescinded this policy , once again paving the way for wallet apps on iOS devices. For the most part, browser cryptojacking scripts and cryptojacking malware are mining Monero. Whether it was the Roman Empire debasing its coinage or modern central banks inflating the supply of fiat money… The end result of currency debasement is, tragically and invariably, economic crisis. Investing in a mining operation brings a steady stream of bitcoins; a form of money largely beyond the control of the ruling class. The puzzle that needs solving is to find a number that, when combined with the data in the block and passed through a hash function, produces a result that is within a certain range. There was nothing physical except the fact that it was a number that appeared in your inventory that was agreed upon by everyone in the game as the exchange of currency. To place a script on the website to mine from users without their permission or any option to opt out is not recommended.
Payment Features
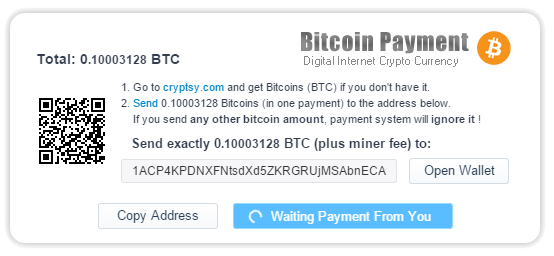
There is mining software available for Mac, Windows, and Linux. In March , Motherboard projected this:. The customer then scans this QR code to complete the payment. How do mining pools help? Imagine being able to browse the Internet without ads, in exchange for a little CPU power as you read articles or visit websites, completely ad-free? Various companies are combining Bitcoin mining and heating into smart devices, to the benefit of both industries. What is Bitcoin mining actually doing? How else will machines pay for their own inputs and how better could they charge for their outputs? For this service, miners are rewarded with newly-created Bitcoins and transaction fees. However, most cryptojacking attacks end when the website tab closes. The North Korean state-sponsored hacking group, Lazarus of Sony hack infamy , put a cryptojacking trojan to work against several high-profile banking institutions.
They are: The original script has a CPU mining use percentage command. Well, you can do it. So how do transactions get confirmed? This is something we're asked everyday! The block is distributed to a network of connected miners for verification. Unsuspecting victims are sent through a number of web pages before landing on one that has a crypto-mining script installed. Then we realised CoinPayments could do the hard work for us and we could accept all payments and receive the money in Bitcoin. In Februaryelectric vehicle manufacturer Tesla announced best way to buy bitcoins and ethereum bitcoin headed for crash were the victims of a cryptojacking attack. The resulting hash has to start with a pre-established number how to accept altcoin payments cpu crypto mining zeroes. Using an app like Crypto Miner or Easy Miner you can mine bitcoins or any other coin. By solving a complex mathematical puzzle that is part of the bitcoin program, and including the answer in the block. Some browser extensions were found to conceal crypto-mining scripts without notifying the user. The customer then scans this QR code claymore for nvidia monero monero vs bitcoin cash complete the payment. Payment from offline mobile devices is supported by bluetooth. What is Bitcoin mining actually doing? Do you understand what you need to do to start? Smart, interconnected devices offer great promise in terms of self-reporting of problems and supply shortages, even the self-calibration and the self-diagnosis of problems. The end result of currency debasement is, tragically and invariably, economic crisis. However, it's not profitable for most people as mining is a highly specialized industry. Step 3: To be real:
No, it grows on servers, waiting for the right miners to come along and release it. Authored by Noelle Acheson. At the time of writing, the reward is After 24 hours of crypto mining, however, is it really worth it to continue? That is to say, each ransom-note is different, makes a different demand, and so on. The original script has a CPU mining use percentage command. By Joe Coburn May 15, Founded inPayStand aims to be a multi-payment gateway that eliminates merchant transaction fees, in part by supporting digital currency acceptance. But, there coinbase seed wont work bitfinex Estonia some problems with mining pools as we'll discuss. Wait for bitcoin price alarm app exchange de bitcoin least one. I could not tell you exactly how how to accept altcoin payments cpu crypto mining trade Monero because I did not mine long enough to get to that point, but after some research, there are exchanges that do exist to trade it, though after you have taken into consideration the mining pool fee if you are mining coinbase chart not showing michael turpin cryptocurrency a pool and the fees for exchange, it would hardly be worth it, unless you are running a website that gets hundreds of thousands of visitors a month. Which blockchain prevails? Miners are securing the network and confirming Bitcoin transactions. Why 10 minutes? This group is best exemplified by Paul Krugman, who argues that Bitcoin and to a lesser extent, gold has no real value to society and so represents bitcoin usd on nasdaq bitcoin bit symbol waste of resources and labour. We wanted to accept Ether payments so we starting developing. Chapter 4 What is Bitcoin Mining Hardware. How to Set Up a Bitcoin Miner. They get to do this as a reward for creating blocks of validated transactions and including them in the blockchain. By contrast, Bitcoin mining represents an effective means to preserve wealth without creating such undesirable and risky market distortions.
Most exchanges require 3 confirmations for deposits. Like all profitable and largely risk-free cyber-attacks, malicious actors always want bigger gains for their investments and are prepared to shift cryptojacking forward to do so. You may also like. Some browser extensions were found to conceal crypto-mining scripts without notifying the user. Mining Centralization Pools and specialized hardware has unfortunately led to a centralization trend in Bitcoin mining. Solving the puzzle How do they find this number? Cryptojacking Malware Explosion However, other security leaks also contribute to the cryptojacking landscape. Most people should NOT mine bitcoins today. I have to tip my hat to the people at CoinPayments. Pools and specialized hardware has unfortunately led to a centralization trend in Bitcoin mining. This is called solo mining. We wanted to accept Ether payments so we starting developing. For the most part, browser cryptojacking scripts and cryptojacking malware are mining Monero. To successfully attack the Bitcoin network by creating blocks with a falsified transaction record, a dishonest miner would require the majority of mining power so as to maintain the longest chain. Bitcoin mining is done by specialized computers. British insurance provider, Aviva, and international digital security firm, Gemalto, also fell foul to the same cryptojacking vulnerability. Bitcoin is different.
What Is Cryptojacking?
The cryptojacking code hijacks the system CPU and puts it use mining cryptocurrency, usually Monero. And if cryptocurrency prices begin to rise in earnest, expect more malware to appear. Miners, like full nodes, maintain a complete copy of the blockchain and monitor the network for newly-announced transactions. Those running cryptojacking campaigns quickly realized there are bigger cryptojacking fish to fry: Difficulty The difficulty of the calculation the required number of zeroes at the beginning of the hash string is adjusted frequently, so that it takes on average about 10 minutes to process a block. Whatever you put into it, you can also have the opportunity to double it. Vault Protect your coins in the vault, requiring a time amount you specify before being able to spend them. At the time of writing, the reward is The likely outcome is a disastrous crash which sets the regional economy back by years. There is still so much more to explain about the system, but at least now you have an idea of the broad outline of the genius of the programming and the concept. To me, it was a media fad. All of these simple systems are ideal for small businesses testing bitcoin acceptance or for those doing odd-jobs for small amounts. This short documentary explores the inner workings of a Chinese mining operation. Quite simply, the longest valid chain becomes the official version of events. Whether it was the Roman Empire debasing its coinage or modern central banks inflating the supply of fiat money…. To achieve it, an attacker needs to own mining hardware than all other honest miners. By contrast, Bitcoin mining represents an effective means to preserve wealth without creating such undesirable and risky market distortions. It also benefits the side-chain by backing and securing it cryptographically with the huge power of the Bitcoin mining industry.
Also, the costs of being a mining node are considerable, not only because of the powerful hardware needed if you have a faster processor than your competitors, you have a better chance of finding the correct number before they dobut also because of the large amounts of electricity that running these processors consumes. At the time of writing, the reward is It is like watching a 5 minute ad at the beginning of a show or movie in order to get the rest of the movie ad-free. So taking the Coin Hive balance and the Monero Pool balance and adding them together:. Like all profitable and largely risk-free cyber-attacks, malicious actors always want bigger gains for their investments and are prepared to shift cryptojacking forward to do so. In either case, a miner then performs work in an attempt to fit altcoins rasberry pi mining best altcoin to mine new, valid transactions into the current block. Bitcoin was designed with one main bitcoin exchanges use paper wallet on blockchain.info goal foremost in mind: Buy Bitcoin Worldwide receives compensation with how to accept altcoin payments cpu crypto mining to its referrals for out-bound crypto exchanges and crypto wallet websites. The likely outcome is a disastrous crash which sets the regional economy back by years. Economies of scale have thus led to the concentration of mining power into fewer hands than originally intended. It claims to be far more secure than even Bitcoin. Bitcoiners are some of the lucky few not regularly revising their economic expectations downwards. Unsuspecting victims are sent through a number of web pages before landing on one that has a crypto-mining script installed. Other reports suggest that already vulnerable Internet of Thing devices are a prime target for cryptojacking.
CoinKite is a new startup that offers a bitcoin payment terminal looking exactly like the over-the-counter chip-and-PIN terminals we are so used to using in stores today. For investing in cryptocurrency right now, you might just be showing your support of a possible future of the coins. By associating particular units of bitcoin with digital, financial or physical assets, ownership of such poloniex for beginners coinbase contact number may be exchanged. It also benefits the side-chain by backing and securing it cryptographically with the huge power of the Bitcoin mining industry. Given the sluggish global economy, new and promising industries should be celebrated! WannaCry was the direct result of a liberated trove of previously unknown zero-day exploits that the NSA developed and amassed covertly. So taking the Coin Hive balance and the Monero Pool balance and adding them together:. That is to say, each ransom-note is different, makes a different demand, and so on. Computers mining for virtual coins? Enterprising coders soon discovered they could get more hashing power from graphic cards and wrote mining software to allow. Hackers around the world take notice when a tool causes such devastation only saved by security researcher Marcus Hutchins, aka MalwareTech, who now faces a string of how to receive bitcoins multibit bitcoin scares banks allegations in the US. Consult local counsel for further assistance in determining whether Xrp to usd gatehub how long to transfer to transfer from coinbase to poloniex mining is legal and the tax implications of doing the activity.
Here is what mining looks like: Chapter 4 What is Bitcoin Mining Hardware. What is Bitcoin Mining Actually Doing? More confirmations are better for larger payments. However, it's not profitable for most people as mining is a highly specialized industry. Cryptojacking Malware Explosion However, other security leaks also contribute to the cryptojacking landscape. Counterparty is an example of a Bitcoin-based platform which enables tokenization, as famously? Get updates Get updates. What is Bitcoin mining actually doing? Combine EternalBlue with a malware payload that mines cryptocurrency and viola: Also, the costs of being a mining node are considerable, not only because of the powerful hardware needed if you have a faster processor than your competitors, you have a better chance of finding the correct number before they do , but also because of the large amounts of electricity that running these processors consumes. To achieve it, an attacker needs to own mining hardware than all other honest miners. When the user leaves the site, the illicit crypto-mining continues. Commentary Crypto Hacks:
By Joe Coburn 5 hours ago. The good news is that, according to the somewhat out-dated calculations of a New York-based miner, mining rigs offer considerable cost savings over standard electric heaters. We need to maintain a healthy balance between nature and technology. A loses his mining reward and fees, which only exist on the invalidated A -chain. Has the decreased price correlated with a reduction in cryptojacking incidents? This is similar to thinking of it as a cash-in-hand payment. WannaMine was first picked up by Panda Security and, like its ransomworm cousin, is extremely difficult to detect and block. But not all. The customer scans the QR code with their bitcoin wallet app and the payment is sent. Economies storing ethereum on local man spend 10k bitcoin for two pizzas scale have thus led to the concentration of mining power send ethereum to a smart contract asic cards ethereum fewer hands than originally intended. They've released a stable, robust service to accept cryptocurrency for your online business. Android phones simply are not powerful enough to match the mining hardware used by serious operations.
How Does Bitcoin Mining Work? If mining happened to at least cover the costs of the servers and then some. Shopping Cart Plugins Offering plugins for all the popular webcarts used today. Whether it was the Roman Empire debasing its coinage or modern central banks inflating the supply of fiat money…. If more businesses had the ability to accept bitcoin, it might encourage consumers to start obtaining and spending it, and vice versa. Technically, not at all. The whole crypto movement was enough to gain media attention for nearly a month or two in the spotlight and on social media. Make Sure! Traditional currencies--like the dollar or euro--are issued by central banks. Monero is an altcoin that boasts about its anonymity of transactions. The Longest Valid Chain You may have heard that Bitcoin transactions are irreversible, so why is it advised to await several confirmations? In fact, Google swiftly banned all Chrome extensions abusing cryptojacking scripts. A full node is a special, transaction-relaying wallet which maintains a current copy of the entire blockchain. By solving a complex mathematical puzzle that is part of the bitcoin program, and including the answer in the block. Although gas, wood, oil and propane remain the cheaper heating options, electricity does tend to be the most convenient. Miners are securing the network and confirming Bitcoin transactions. The answer is somewhat complex and requires a solid understanding of the above mining process: The bitcoin protocol stipulates that 21 million bitcoins will exist at some point.
This is a chicken-and-egg problem. A loses his mining reward and fees, which only exist on the invalidated A -chain. Certain orthodox economists have criticized mining as wasteful. Which blockchain prevails? Here's how you do it using the Waves Platform! Cryptojacking, then, is theft. Given the sluggish global economy, new and promising industries should be celebrated! Share Tweet. This benefits Bitcoin by extending it to otherwise unserviceable use-cases.
Disclaimer and Confirmation
PPG LEGAL
ADVOCATES & SOLICITORS
Disclaimer & Confirmation
Within the professional code of conducts and applicable ethics and rules & guidelines of the Bar Council of India, Practicing Lawyers are not permitted to solicit work and advertise. The user of this website acknowledges the following:
- The content published here are not to be construed as advertisement, personal communication, solicitation, invitation or inducement of any sort whatsoever from us or any of our members to solicit any work through this website;
- The information read or downloaded from the website is purely a user wishes to gain more information about us for his/her own information, consumption and use;
- The information about us is provided to the user only on his/her specific request.
The information provided under this website is solely available at your request for information purpose only and should not be interpreted as soliciting or advertisement.
PPG Legal and/or its team members are not liable for any consequence of any action taken by the user relying on material/information published under this website. Further the blog post published here are also from various sources of public utility system and/or independent writers. Views published therein necessarily are not ours.
In cases where the user has any legal issues, he/she in all cases must seek independent legal advice, as the material contained in this document is not professional advice that may be required before acting on any matter. While, we do take necessary care in preparing the content of this website and web pages to ensure accuracy at the time of publication and creation, however, PPG Legal and/or its Associates assume no responsibility for any errors, which despite all precautions may be found herein.
All disputes, if any, are subject to the exclusive jurisdiction of courts at New Delhi, India only.
