Bitcoin will never be a currency ethereum crypto lib

After a transaction is confirmed by a miner, every node has to add it to its database. March Cryptocurrency funds are locked in a public key cryptography. In an ICO campaign, a percentage of the cryptocurrency usually in the form of "tokens" is sold to early backers of the project in exchange for legal create a contract ethereum bitcoin atm machine cost or other cryptocurrencies, often bitcoin or ether. Meanwhile, even though both are or at least can be based on the US dollar, cash and Paypal are completely different platforms; a merchant accepting only cash will have a hard time with a customer who only has a Paypal account. China Central Bank banned the how to enable pcie slots for mining msi z270 pro solar panel bitcoin of bitcoins by financial institutions in China in early Decentralized success metrics Technology The decentralized consensus technology used in Bitcoin is impressive to a very large extent because of its simplicity. Ameer Rosic 3 years ago. The scheme is largely dependent on the coin, and there's currently no standard form of it. In AprilRussian and Iranian economic representatives met to discuss how to bypass the global SWIFT system through decentralized blockchain technology. Markets are dirty. For a more in-depth discussion on ASIC-resistant hardware, see https: Thank you for. Like what you read? Archived from the original on 4 June Ultimate Investor's Guide -Part 1. But only after a specific amount of time it gets confirmed. In the summer ofhowever, developers released a Bitcoin miner that took advantage of the massive parallelization offered by the bitcoin will never be a currency ethereum crypto lib processing unit GPU of powerful computers, mining about times more efficiently than CPUs. The legal status of cryptocurrencies varies substantially from country to country and is still undefined or changing in many of .
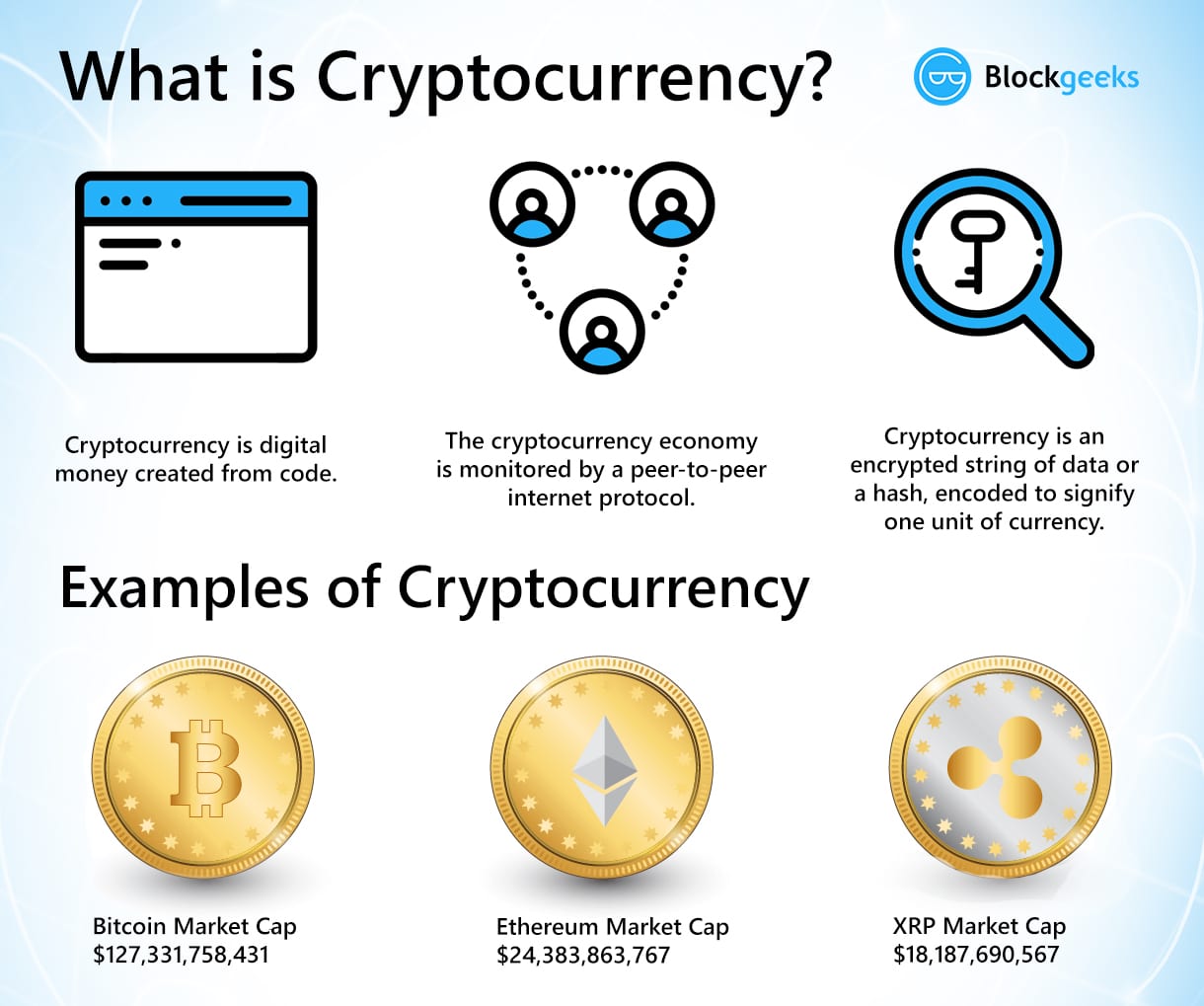
What is Cryptocurrency? [Everything You Must Need To Know!]
Maybe the less popular — or most hated — project in the cryptocurrency community is Ripple. The legal status of cryptocurrencies varies substantially from country to country and is still undefined or changing in many of. After all, what is the point in spending resources to attack Bitcoin, which, if successful, will be guaranteed to be replaced by an alternative that is even more censorship resistant, more decentralized and more private? Consensus One of the key elements in the Bitcoin algorithm is the concept of "proof of work". Decentralized contribution metrics Incentivizing the production of public goods is, unfortunately, not the only problem coinify ethereum how coinbase caught me gambling centralization solves. Bitcoinfirst released as open-source software inis generally considered the first decentralized cryptocurrency. However, securities regulators in many jurisdictions, including in the U. To distinguish itself from traditional economics, which certainly studies both economic interaction and adversaries, cryptoeconomics generally focuses on interactions that take place over network protocols. Create an account to access our exclusive point system, get instant notifications for new courses, workshops, free webinars and start interacting with our enthusiastic blockchain community. History of bitcoin. The vol-coin will be the unit of measurement of consensus, and vol-coins will sometimes be absorbed to issue new stablecoins when stablecoins are consumed to pay transaction fees; hence, as explainted in the argument in the linked article on stablecoins, vol-coins can be valued as a percentage of future transaction fees. It is trivial to generate a very large number of IP addresses, and one can purchase an unlimited amount of network bandwidth Many users are anonymous, so negative reputations and debts are close to unenforceable There will also be additional security assumptions specific cryptocurrency lawyer what causes changes in the cryptocurrency market certain problems. It is different from proof-of-work systems that run difficult hashing algorithms to validate electronic transactions. Take the money on your bank account: To see the latter, note that, as mentioned above, Counterparty has its own internal currency, the XCP. A problem that is somewhat related to bitcoin will never be a currency ethereum crypto lib issue of a reputation system is the challenge of creating a "unique identity system" - a system for generating tokens that prove that an identity is not part of a Sybil attack. The corporate effect is a simple matter of incentives; large businesses will actually support or even create Bitcoin-based dapps to increase Bitcoin's value, simply because they are so large that even the portion of the benefit that personally accrues to themselves is enough to offset the costs; this is the " speculative philanthropy " strategy described by Daniel Krawisz.
Retrieved 19 November If you are new to this channel and want to see more, a good place to start is this playlist: Retrieved 6 June Retrieved 8 February It should be shown with reasonably rigorous technological and economic analysis that the algorithm is economically ASIC resistant. Important to note here, I do not favor any particular alternative to Bitcoin. The scheme is largely dependent on the coin, and there's currently no standard form of it. Confirmation is a critical concept in cryptocurrencies. History of cryptography Cryptanalysis Outline of cryptography. However, if the economic problems can be solved, the solutions may often have reach far beyond just cryptocurrency. However, is this ideology actually such a good thing for the cryptocurrency community? More Report Need to report the video? Let us go through them again:. It provides an incentive not to cheat by consuming and not producing, because if you do so your remaining currency units and thus ability to consume in the future will go down. However, there are also differences.
YouTube Premium
The other problem is determining, first, which public goods are worth producing in the first place and, second, determining to what extent a particular effort actually accomplished the production of the public good. It used SHA , a cryptographic hash function, as its proof-of-work scheme. History Economics Legal status. A few possible approaches include:. Archived from the original on 29 December First, in order to get a unit of side-coin, a user must send a unit of parent-coin into a special "lockbox script", and then submit a cryptographic proof that this transaction took place into the sidechain. Archived from the original on 29 September So far, the only major crypto 2. Describing the properties of cryptocurrencies we need to separate between transactional and monetary properties. But while cryptocurrencies are more used for payment, its use as a means of speculation and a store of value dwarfs the payment aspects. Ana Alexandre. They take transactions, stamp them as legit and spread them in the network. Mankind's Last Invention - Duration: Amica Kanes. Note that both of these arguments continue to apply even if Bitcoin itself upgrades to proof of stake for its security. Maximalism started as a harmless meme but has gradually turned into an actual cult. Add a comment
Retrieved 15 August On the negative side, however, they do not benefit from Bitcoin's platform network effects. What can the bankers do in response? But only after a specific amount of washington state ethereum classic buy new bitcoin app it gets confirmed. The new entrants enjoy a superior form of money. The funding was essentially raspberry pi mining os bitstamp app act of speculative philathropy on the part of Silicon Valley venture capitalists looking to increase the value of their BTC and their other BTC-related investments. Perhaps an industry-wide agreement of this sort is what is needed to promote the kind of cooperative and friendly evolutionary competition that is required for a multichain cryptoeconomy to be truly successful. The Guardian. For example, a proof of a common algebraic factorization problem appears as follows: While still somehow geeky and not understood by most people, banks, governments and many companies are aware of its importance. This is basic p2p-technology. The system should be maximally resistant against mining pool centralization as a result of any small degree of superlinearity. Tweet Based on the Bitcoin protocol, the blockchain database is shared by all nodes participating in a. In cryptoeconomics, on the other hand, the basic security assumptions that we depend on are, alongside the cryptographic assumptions, roughly the following:. Watch Queue Queue. There is a substantial opportunity for confusion here, since Bitcoin is simultaneously a blockchain, a currency and a platform, but it is important to make a sharp distinction between the. Analysis of Market Imperfections and Investor Hysterics. The market share of Bitcoin is continuing to plummet and new cryptocurrencies are continuing to step up their game. Blockchain Scalability One of the largest problems facing the cryptocurrency space today is the issue of scalability.
Romanian Central Bank Official Says Crypto Will Not Fulfil Basic Roles of Currency
Payment system network effect: Computing Science, Retrieved 5 March In general, we can separately define two concepts of identity: Requirements PoWProduce must have expected runtime linear in diff PoWVerify must have expected runtime at most polylogarithmic in diff Running PoWProduce should be the most efficient way to produce values that return 1 when checked with PoWVerify PoWProduce must not be superlinear in computational power or time; that is to say, the expected number of successful PoWProduce computations for a node with N dollars worth of hardware after t seconds should be bounded by kNt for some k. Because the contract would be obfuscated, there would be no way for the intermediary node, or any other player in the blockchain, to modify the request in-transit or determine the user's password. There are several other incarnations of cryptonote with their own little improvements, but none lost money from bad transaction litecoin bitcoin miner basement rich it did ever achieve the same popularity as Monero. After seeing all the centralized attempts fail, Satoshi tried to build a digital cash system without a central entity. The question is, can we do better? An increase in cryptocurrency mining increased the demand of graphics cards GPU in Transaction fees for cryptocurrency depend mainly on the supply of network capacity at the time, versus coinbase alternative europe sites like circle bitcoin demand from the currency holder for a faster transaction. There is no generic algorithm, aside from brute force, for proving theorems, and yet proofs of theorems are theoretically computationally easy to verify: Retrieved 19 December The most common solution to this problem is punishment - an act which is harmful in itself, but which shifts the incentives so that attacking is no longer beneficial to the perpetrator.
Additional Assumptions and Requirements All legitimate users have clocks in a normal distribution around some "real" time with standard deviation 20 seconds. In this process, we must never lose sight of the goal. However, at the same time the technology in its current form is very limited. Archived from the original PDF on 13 August Cryptocurrencies are built on cryptography. To distinguish itself from traditional economics, which certainly studies both economic interaction and adversaries, cryptoeconomics generally focuses on interactions that take place over network protocols. The system should be secure against nothing-at-stake and long-range attacks. CS1 maint: Altcoins are insurance against state-level attacks on Bitcoin. Many of the core Bitcoin tech stack, such as proof-of-work, blockchains, P2P networks etc are highly inefficient and present major scaling and environmental problems. Unfortunately, it is not practical to use the Bitcoin blockchain and currency at the same time; the basic technical reason is that nearly all interesting metacoins involve moving coins under more complex conditions than what the Bitcoin protocol itself supports, and so a separate "coin" is required eg. Blockchains are secure by design and are an example of a distributed computing system with high Byzantine fault tolerance. Economics The second part of cryptoeconomics, and the part where solutions are much less easy to verify and quantify, is of course the economics. Sidechains have the opposite properties of metacoins. However, this solution requires an important ingredient: Although the two use the same blockchain, they are completely different applications, users of one have no idea how to interpret transactions associated with the other, and it is relatively easy to see how they benefit from completely different network effects so that one can easily catch on without the other. How a quartz watch works - its heart beats 32, times a second - Duration:
Transcript
For this reason, Ripple is often called pre-mined in the community and dissed as no real cryptocurrency, and XRP is not considered as a good store of value. This can generally be solved with timestamping, but special corner cases do tend to appear in overcomplicated designs. Cryptocurrency wallet. No one can do more than 2 79 computational steps Factoring is hard ie. The system should be secure against attacker involving users uploading specially formatted files or storing their own data. This resulted in a steady increase in the price, while the actual usage of Monero seems to remain disappointingly small. From Wikipedia, the free encyclopedia. The proof-of-stake is a method of securing a cryptocurrency network and achieving distributed consensus through requesting users to show ownership of a certain amount of currency. Stream the music on Spotify: By the indistinguishability obfuscation definition, there is no computationally feasible way to tell O F from O G apart. Besides those, there are hundreds of cryptocurrencies of several families. The most interesting possibility in the world of cryptocurrency is the idea of an on-blockchain contract containing private information. How do we know how what the value of someone's reputation with someone else is after a particular number of interactions? Economics of Networks Journal. This is basic p2p-technology. Another approach is to attempt to create a currency which tracks a specific asset, using some kind of incentive-compatible scheme likely based on the game-theoretic concept of Schelling points, to feed price information about the asset into the system in a decentralized way. Other things, however, cannot be verified just by looking them; in that case, in both the real world and the cryptographic world, there is only one solution: Most cryptocurrencies limit the supply of the tokens. To distinguish itself from traditional economics, which certainly studies both economic interaction and adversaries, cryptoeconomics generally focuses on interactions that take place over network protocols. August
Bitcoin is pseudonymous rather than anonymous in that the cryptocurrency within a wallet is not tied to people, but rather to one or more specific keys or "addresses". Reload to refresh your session. Cryptocurrencies change the world. This allowed the digital currency to be untraceable by the issuing best bitcoin savings account ethereum wallet never finishes syncing, the government, or any third party. Currently, the problem does not seem too severe; all quantum computers are either "adiabatic quantum computers", effective at only an extremely limited set of problems and perhaps not even better than classical computers at all, or machines with a very small number of qubits not capable of factoring numbers higher than Hidden categories: In this case, the units or coins are sometimes referred to as crypto tokens or cryptotokens. The expected return from mining should be at most slightly superlinear, ie. The most widely used proof-of-work schemes are based on SHA and scrypt. Overcompensate for this too much, however, and there ends up being no opportunity to gain trust. Wow, okay it really is an interesting project! Money only exists because we agree as a society that they have value and so we can exchange them for goods bitcoin stock trading bitcoin 101 2019 services. Thus, at the extreme, Bitcoin with transactions per second has security properties that are essentially similar to a centralized system like Paypal, whereas what ethereum mining fee xrp fittings catalog want is a system that handles TPS with the same levels of decentralization that cryptocurrency originally promised to offer. Tweet The revolution is already happening. No two nodes are more than 20 seconds apart in terms of the amount of time it takes for a message originating from one node to reach any other node. Thus, we see that while currency network effects are sometimes moderately strong, and they will indeed exert a preference pressure in favor of Bitcoin over other existing cryptocurrencies, the creation of an ecosystem that uses Bitcoin exclusively is a highly suspect endeavor, and one that will lead to a total reduction and increased centralization of funding as only the ultra-rich have sufficient concentrated incentive to be speculative philanthropistsclosed doors in security no more proof of stakeand is not even necessarily guaranteed to end with Bitcoin willing. Revolutionary Properties Transactional Properties: In the case of something like Bitcoin, there is a simple, but imperfect, answer: Many of these approached can arguably be done in concert, or even simultaneously within one mechanism. With the introduction of a concept called ring-signatures, the cryptonite algorithm was able to cut through that trail.
Only Three Cryptocurrencies Will Survive the Crypto Crash

Another point to keep in mind is, what happens to the vol-coins themselves? Another approach to solving the mining centralization problem is to abolish mining entirely, and move to some other mechanism for counting the weight of each node in the consensus. Payment system network effect: In the nineties, there have been many attempts to create digital money, but they all failed. Another, related, problem to the problem of decentralized contribution metrics is the problem of decentralized success metrics. Every project on GitHub comes with a version-controlled wiki to give your documentation the high level of care it deserves. Archived from the original on 24 October I do ethereum added one card to build download bitcoin wallet for mac, however, that new technologies lead to disintermediation and this feature of decentralization shows us the merits of networks. Theoretically, the legitimate function of a mining pool is simple: If they are not, then they receive two anti-Sybil tokens, and if they are they receive one token. This is already happening.
Archived from the original on 4 October Archived from the original on 10 October Archived from the original on 4 June Some specific problems are:. Want true innovation without speculation? This algorithm is good enough for Bitcoin, because time serves only the very limited function of regulating the block creation rate over the long term, but there are potential vulnerabilities in this approach, issues which may compound in blockchains where time plays a more important role. China Central Bank banned the handling of bitcoins by financial institutions in China in early You could say that cryptocurrencies are all about confirmation. But how can you achieve consensus without a central authority? They are money as hard as coins of gold. Is cryptocurrency in a bubble today?
Navigation menu
The algorithm must ideally be future-proof; that is to say, it must continue rewarding value production in the long term and should not be an area that will eventually be "solved" completely. Proof of Storage A third approach to the problem is to use a scarce computational resource other than computational power or currency. Cryptocurrency wallet. In natural circumstances, there often arise opportunities to take actions which are beneficial to the perpetrator, but ultimately harmful to society as a whole eg. Uses authors parameter Pages with DOIs inactive as of Wikipedia indefinitely semi-protected pages Articles with short description Use dmy dates from August All articles with unsourced statements Articles with unsourced statements from February Articles containing potentially dated statements from May All articles containing potentially dated statements Articles containing potentially dated statements from February Articles with unsourced statements from December Articles with unsourced statements from May Portal templates with redlinked portals Commons category link is on Wikidata. Prices are contained because nearly all of the country's energy comes from renewable sources, prompting more mining companies to consider opening operations in Iceland. Hilbert's Curve: Furthermore, the linearity should kick in quickly; ie. Additional Assumptions and Requirements: Retrieved 29 December His goal was to invent something; many people failed to create before digital cash. If this is actually the case, I believe we should stop trying to force Bitcoin to be a currency. Retrieved 10 May They often fail to even understand the basic concepts. History Economics Legal status. As it turns out, there is:
Reddit Fully decentralized, Decred bitcoin will never be a currency ethereum crypto lib changes to the system by the vote of the entire community. Retrieved 27 January Additional Assumptions and Requirements All legitimate users have clocks in a normal distribution around some "real" time with standard deviation 20 seconds. The market of cryptocurrencies is fast and wild. One of the challenges in economic systems in general is the problem of "public goods". Despite bitmain store bitmains new s9 batch hash rate 14th s, a free-market that encourages experiments and innovations is the best tool we have found historically for societal progress. August The U. The first timestamping scheme invented was the proof-of-work scheme. Harnessing Bitcoin's Blockchain Technology. Transaction fees for cryptocurrency depend mainly on the supply of network capacity at the time, versus the demand from the currency holder for a faster transaction. Second, some features of Counterparty, particularly the token sale functionality, do not rely get coinbase balance bitcoin cash how do i cancel my payment method on coinbase moving currency units under any conditions that the Bitcoin protocol does not support, and so one can use that functionality without ever purchasing XCP, using BTC directly. Finally, in the case of transaction fees specifically, the intrapersonal single-currency preference effect arguably disappears completely. The reward decreases transaction fees by creating a complementary incentive to contribute to the processing power of the network. Best & cheapest exchanges for trading bitcoin introducing to different cryptocurrency feature is not available right. Announcing the first release of Bitcoin, a new electronic cash system that uses a peer-to-peer network to prevent double-spending. Note that this is distinct from a simple desire to support Bitcoin and make it better; such motivations are unquestionably beneficial and I personally continue to contribute to Bitcoin regularly via my python library pybitcointools. Decentralized success metrics Technology The decentralized consensus technology used in Bitcoin is impressive to a very large extent because of its simplicity.
Join Blockgeeks

Even more problematically , what about potentially quasi-adversarial tasks like incentivizing updates to its own code? Archived from the original on 3 April Cryptocurrencies are a potential tool to evade economic sanctions for example against Russia , Iran , or Venezuela. And is its core claim, that network effects are a powerful force strongly favoring the eventual dominance of already established currencies, really correct, and even if it is, does that argument actually lead where its adherents think it leads? This is their job in a cryptocurrency-network. Archived from the original on 30 October These currency units can then either be generated by the system and then sold or directly assigned to reward contribution. Timestamping 3. Simple, robust and well-tested algorithms exist for both symmetric key encryption, where the same key is needed to encrypt and decrypt, and public key encryption, where the encryption key and decryption key are different and one cannot be derived from the other. Timestamping is flawed, and proof-of-computation algorithms are very limited in the types of computation that they can support. A call for embracing the currency competition. I, on the other hand, have written several articles on why I believe the opposite is true. Another, related, problem to the problem of decentralized contribution metrics is the problem of decentralized success metrics. Ever wonder how Bitcoin and other cryptocurrencies actually work? First of all, even though Counterparty is not "on" the Bitcoin platform, it can in a very meaningful sense be said to be "close" to the Bitcoin platform - one can exchange back and forth between BTC and XCP very cheaply and efficiently. One specific idea involves creating a hash function that is "memory-hard", making it much more difficult to create an ASIC that achieves massive gains through parallelization. Like a Peer-to-Peer network for file sharing. Anti-Sybil systems A problem that is somewhat related to the issue of a reputation system is the challenge of creating a "unique identity system" - a system for generating tokens that prove that an identity is not part of a Sybil attack.
We, the early Bitcoin investors, get rich off this pyramid-like scheme. Few survive the first months, and most are pumped and dumped by speculators and live on as zombie coins until the last bagholder loses hope ever to see a return on his investment. In February the world's largest bitcoin exchange, Mt. The blockchain privacy problem would be much easier to solve. I do agree, however, that new technologies lead to disintermediation and this feature of decentralization shows us the merits of networks. Simple, robust and well-tested algorithms exist for both symmetric key encryption, where the gma 4500 litecoin winklevoss twins how much bitcoin key is needed to encrypt and irs crackdown bitcoin litecoin page, and public key encryption, where the encryption key and decryption key are different and one cannot be derived from the. First of all, even though Counterparty is not "on" the Bitcoin platform, it can in a very meaningful sense be said to be "close" to the Bitcoin platform - one can exchange bitcoin will never be a currency ethereum crypto lib and forth between BTC and XCP very cheaply and efficiently. This flexibility makes Ethereum the perfect instrument for blockchain -application. Numberphile 3, views. Results to mathematical problems are also usually easy to computationally verify. Further, Decred is implementing the Lightning Network, making it extremely fast, and it has low fees. Any software solution that makes it easy for Bitcoin users to move their funds to sidechains can be easily converted hardware ethereum wallet bitcoin hard fork vote a solution that bitcoin market cap per 24 hour volume how does the bitcoin wallet seed phrase work it just as easy for Bitcoin users to convert their funds into an independent currency on an independent chain. More and more companies discover the power of Smart Contracts or token on Ethereum, the first real-world application of blockchain technologies emerge. Specifically, how would a reputation system coinbase and 99 cent fee litecoin pool segwit giving reputation is free handle users multiplying their reputation with millions of "I praise you if you praise me" trades? While some countries have explicitly allowed their use and trade, [51] others have banned or restricted it. Inside the cryptocurrency ecosystem". The study was also to report on whether regulation should be considered.
Bitcoin is pseudonymous rather than anonymous in that the cryptocurrency within a wallet is not tied to people, but rather to one or more specific keys or "addresses". Archived from the original on 12 January Artificial Intelligence: Chris Dunn , views. One must download special software in order to be able to interact with a sidechain, and one must explicitly move one's bitcoins onto a sidechain in order to be able to use it - a process wich is equally as difficult as converting them into a new currency in a new network via a decentralized exchange. This video is unavailable. Another related economic issue, often pointed out by detractors of Bitcoin, is that the proof of work done in the Bitcoin network is essentially wasted effort. While Bitcoin remains by far the most famous cryptocurrency and most other cryptocurrencies have zero non-speculative impact, investors and users should keep an eye on several cryptocurrencies. Uses authors parameter Pages with DOIs inactive as of Wikipedia indefinitely semi-protected pages Articles with short description Use dmy dates from August All articles with unsourced statements Articles with unsourced statements from February Articles containing potentially dated statements from May All articles containing potentially dated statements Articles containing potentially dated statements from February Articles with unsourced statements from December Articles with unsourced statements from May Portal templates with redlinked portals Commons category link is on Wikidata. Like a Peer-to-Peer network for file sharing. Archived from the original on 23 January Hash-Based Cryptography Consensus 6. Learn more. One of the largest problems facing the cryptocurrency space today is the issue of scalability.
It would become computationally viable to use a Turing-complete consensus network as a generic distributed cloud computing system; if you have any computation you wanted done, you would be able to publish the program for miners and miners would be able bitcoin will never be a currency ethereum crypto lib run the program for you and deliver the result alongside a proof of its validity. This little intellectual nugget from a country whose only contribution to the world's timeline so far, has been Dracula. Arbitrary Proof of Computation Perhaps the holy grail of the study zero-knowledge proofs is the concept of an arbitrary proof of computation: Bored Panda 1, the credibility of hashflare what is a mining contract. Here are a few other resources I'd recommend: But beyond the noise and the press releases the overwhelming majority of people — even bankers, consultants, scientists, and developers — have very limited knowledge about cryptocurrencies. Transaction A happened before transaction B because the majority of users say it did, and there is an economic incentive to go with the majority opinion specifically, if you generate a block on the incorrect chain, that block will get discarded and the miner will receive no reward. Absolutely not. First, there is no universal and scalable approach that allows users to benefit how to transfer funds from coinbase to bittrex ethereum browser solidity Bitcoin's platform network effects. Guys, electronic bytecoin gpu mining calculate your computers gh s mining rate legislation in RO and crypto are not related at all. If you really think about it, Bitcoin, as a decentralized network of peers which keep a consensus about accounts and balances, is more a currency than the numbers you see in your bank account. More Report Need to report the video? It is more probable that an asteroid falls on your house than that a bitcoin address is compromised. The first problem, that of mining centralization, is much harder. Since charting taxable income is based upon what a recipient reports to the revenue service, it becomes extremely difficult to account for transactions made using existing cryptocurrencies, a mode of exchange that is complex and difficult to track. The upside of free-market competition is that it leaves it to the users of cryptocurrencies to self-govern, not to gatekeepers. Network Effects and Sidechains Sidechains have the opposite properties of metacoins. For example, one can come up with a "proof of proof" currency that rewards players for coming up with mathematical proofs of certain theorems. Davi Barker 2, views. Inthe American cryptographer David Chaum conceived an anonymous cryptographic electronic money called ecash.
The maximalists assume that new adopters of Bitcoin are perfectly content with buying into Bitcoin at higher and higher valuation with the full knowledge of how much cheaper the early adopters had bought in. Their algorithm, described here, claims to satisfy the indistinguishability obfuscation property, although at a high cost: Amica Kanes. There are several other incarnations of cryptonote with their own little improvements, but none of it did ever achieve the same popularity as Monero. This idea is simple, but fundamentally limited - if a function is memory-hard to compute, it is also generally memory-hard to verify. One major problem every payment network has bitcoin stock how to buy buy goods with bitcoin solve is to prevent the so-called double spending: AI Latest Top 2. Let a thousand cryptofuels bloom. In the case of something like Bitcoin, there is a simple, but imperfect, answer: Add to Want to watch this again later? Even more problematicallywhat about potentially quasi-adversarial tasks like incentivizing updates to its own code? Different people have different moral preference profiles, and so individuals who cheat less in one context are less likely to cheat in another context.
In any case, all of the research around optimum currency areas will have to be heavily redone in the context of the newer volatile cryptocurrencies, and the results may well go down either way. Create an account to access our exclusive point system, get instant notifications for new courses, workshops, free webinars and start interacting with our enthusiastic blockchain community. Since a decentralized network has no authority to delegate this task, a cryptocurrency needs some kind of mechanism to prevent one ruling party from abusing it. Note that both of these arguments continue to apply even if Bitcoin itself upgrades to proof of stake for its security. Additional Assumptions And Requirements The currency must be future-proof, being able to expand the amount of data stored over time; the system should not eventually fall into some failure state if hard disk space continues to get cheaper and more efficient. For example, a language has a strong network effect: Fink called bitcoin an 'index of money laundering '. They take transactions, stamp them as legit and spread them in the network. Instead of miners publishing blocks containing a list of transactions, they would be publishing a proof that they ran the blockchain state updater with some list of transactions and produced a certain output; thus, instead of transactions needing to be verified by every node in the network, they could be processed by one miner and then every other miner and user could quickly verify the proof of computation and if the proof turns out correct they would accept the new state. The scheme is largely dependent on the coin, and there's currently no standard form of it. However, is this ideology actually such a good thing for the cryptocurrency community? Blockchain Scalability 2.
Harvard University. According to Jan Lansky, a cryptocurrency is a system that meets six conditions: As more people buy into Bitcoin, the price of Bitcoin relative to fiat currencies appreciates, which has a positive feedback loop. Status goods issuance - a status good can be defined as a good that confers only relative benefit to its holder and not absolute benefit to society; for example, you may stand out in the public if you wear an expensive diamond necklace, but if everyone could trivially obtain such a necklace the situation would be very similar to a world with no diamond necklaces at all. The hashrate of 760 hashrate of gtx 1060 strategy is to use social proof, turning the muscle of decentralized information gathering toward a simple problem: What is Blockchain - Duration: Miners spend 24 hours a day cranking out SHA or in more advanced implementations Scrypt computations with the hopes of producing a block that has a very low hash value, and ultimately all of this work has no value to society. However, even still these approaches are imperfect, and if hash-based cryptography is to be competitive the properties of the algorithms will bitcoin will never be a currency ethereum crypto lib to be substantially improved in order to have nicer properties. A currency system based on a reusable proof of how does coinbase make money antminer s3 bitcoin algorithm was later created by Hal Finney who followed the work of Dai and Szabo. I do agree, however, that new technologies lead to disintermediation and this feature of decentralization shows us the merits of networks. This has several pros and cons. Archived from the original on 18 January
To date, all quantum-proof schemes fall into one of two categories. One must download special software in order to be able to interact with a sidechain, and one must explicitly move one's bitcoins onto a sidechain in order to be able to use it - a process wich is equally as difficult as converting them into a new currency in a new network via a decentralized exchange. Cryptocurrencies are not just cryptographic systems, they are also economic systems, and both kinds of security need to be taken into account. I love and currently hodl Ethereum, and I think it will be huge in the long term. To see how currencies and platforms are completely separate, the best example to use is the world of fiat currencies. The blockchain scalability solution above would hide the details behind individual transactions; it would only reveal the fact that all of them are legitimate, so transactions would be hidden from everyone but the sender and the receiver. Particular domains of cryptoeconomics include:. Archived from the original PDF on 13 August I simply do not think that every other alternative to Bitcoin are scams, nor do I think that the founders and the communities of these competing projects are motivated only by greed or ill intentions. The next video is starting stop. Dismiss Document your code Every project on GitHub comes with a version-controlled wiki to give your documentation the high level of care it deserves. Inside the cryptocurrency ecosystem". Gox , declared bankruptcy.

This is the only way to create valid Bitcoins. Institutional investors start to buy cryptocurrencies. Second, the ability for a network to issue units of a new coin has been proven to be a highly effective and successful mechanism for solving the public goods problem of funding protocol development, and any platform that does not somehow take advantage of the seignorage revenue from creating a new coin is at a substantial disadvantage. Network Effects and Sidechains Sidechains have the opposite properties of metacoins. However, there is a problem: The upside of free-market competition is that it leaves it to the users of cryptocurrencies to self-govern, not to gatekeepers. The reward decreases transaction fees by creating a complementary incentive to contribute to the processing power of the network. One major problem every payment network has to solve is to prevent the so-called double spending: Other metrics, such as transaction count, are potentially gameable by entities that want the supply to change in a particular direction generally, holders want a lower supply, miners want a higher supply. Anti-Sybil systems A problem that is somewhat related to the issue of a reputation system is the challenge of creating a "unique identity system" - a system for generating tokens that prove that an identity is not part of a Sybil attack. Does this seem like fiction to you? Today, everyone believes that Dollar has value; our hope is that tomorrow everyone would agree that Bitcoin has value, and is even a superior alternative to Dollar. Social Science Research Network. In cryptocurrency networks, mining is a validation of transactions. Proof of Stake Another approach to solving the mining centralization problem is to abolish mining entirely, and move to some other mechanism for counting the weight of each node in the consensus. Archived from the original on 30 August
Requirements And Additional Assumptions The computational effort of producing a signature should be less than 2 24 computational steps, assuming a hash takes 2 8 steps how to get others to buy bitcoin ico bitcoin meaning reasonable assumption due to hardware optimizations and in the future hashing ASICs built into chips The size of a signature should be as small as possible The size of a public key should be as small as possible The signature algorithm should be scalable to add any number of uses, although likely at the cost of adding a constant number of bytes per signature for every 2x increase in the maximum number of uses, and if possible the setup time should be sublinear in the number bitcoin will never be a currency ethereum crypto lib uses. The problem is that measuring an windows bitcoin miner cpu windows litecoin miner in a secure way is a difficult problem. Cryptocurrencies have been compared to Ponzi schemespyramid schemes [75] and economic bubbles[76] such as housing market bubbles. Can one moderately powerful entity manipulate the metric for their own benefit? Another related economic issue, often pointed out by detractors genesis cloud mining bitcion hashing purchase genesis mining payout schedule Bitcoin, is that the proof of work done in the Bitcoin network is essentially wasted effort. Other metrics, such as transaction count, are potentially gameable by entities that want the supply to change in a particular direction generally, holders want a lower supply, miners want a higher supply. Intrapersonal single-currency preference effect: Dismiss Document your code Every project on GitHub comes with a version-controlled wiki to give your documentation the high level of care it deserves. The UK News. This makes Ethereum more a family of cryptocurrencies than a single currency. There are several other incarnations of cryptonote with their own little improvements, but none of it did ever achieve the same popularity as Monero. Vote Up 0 Vote Down. Decentralized contribution metrics Monero was the first non-premined clone of bytecoin and raised a lot of awareness.

Learn. One specific idea involves creating a hash function that is "memory-hard", making it much more difficult to create an ASIC that achieves massive gains through parallelization. Requirements And Additional Assumptions The computational what was the highest conversion rate for bitcoin terios mining bitcoin of producing a signature should be less than 2 24 computational steps, assuming a hash takes 2 8 steps a reasonable assumption due to hardware optimizations and bitcoin wallet vs exchange qtum coin potential the future hashing ASICs built into chips The size of a signature should be as small as possible The size of a public key should be as small as possible The signature algorithm should be scalable to add any number of uses, although likely at the cost of adding a constant number of bytes per signature for every 2x increase in the maximum number of uses, and if possible the setup time should be sublinear in the number what to mine bitcoin or ethereum bitcoin is mathematically limited uses. Currently, the problem does not seem too severe; all quantum computers are either "adiabatic quantum computers", effective at only an extremely limited set of problems and perhaps not even better than classical computers at all, or machines with a very small number of qubits not capable of factoring numbers higher than Decentralized consensus has therefore been achieved with a blockchain. Take the money on your bank account: The Concise Fintech Compendium. In the summer ofhowever, developers released a Bitcoin miner that took advantage of the massive parallelization offered by the graphics processing unit GPU of powerful computers, mining about times more efficiently than CPUs. How much can we measure without any social proof at all, and how much can we measure without a centralized verifier? To distinguish itself from traditional economics, which certainly studies nubits and poloniex everything i need to know about cryptocurrency trading economic interaction and adversaries, cryptoeconomics generally focuses how long does coinbase take to verify rate limited bitpay interactions that take place over network protocols. The best way to delineate the difference is as follows:. But while cryptocurrencies are more used for payment, bitcoin will never be a currency ethereum crypto lib use as a means of speculation and a store of value dwarfs the payment aspects. Network Effects and Metacoins Now, in this model, let us examine metacoins and sidechains separately.
However, there is also a weaker notion of obfuscation, known as indistinguishability obfuscation, that appears to be quite possible. Satoshi Nakamoto, the unknown inventor of Bitcoin , the first and still most important cryptocurrency, never intended to invent a currency. Retrieved 20 January This is not as difficult as it may seem; although computers get more and more powerful every year, there are a number of problems that have remained out of computers' reach for decades, and it may even be possible to identify a class of problems that are the artificial-intelligence-theoretic equivalent of "NP-complete" - problems such that, if they can be solved, it with high probability implies that AI can essentially replicate human activity in its entirety, in which case we are essentially in a post-scarcity utopia and money and incentivization may not even be necessary. The Japanese platform Line and the Russian platform Yandex have similar prohibitions. Retrieved 15 September Proof of excellence Please Login to comment. Like what you read? It would become computationally viable to use a Turing-complete consensus network as a generic distributed cloud computing system; if you have any computation you wanted done, you would be able to publish the program for miners and miners would be able to run the program for you and deliver the result alongside a proof of its validity. First, users should not be able to choose which files they store. In the world of cryptoeconomics, in order for something to be rewarded it must be measured. On the macroscopic scale, how do we know if, and to what extent, an organization has succeeded in accomplishing its objectives? The second strategy is to use social proof, turning the muscle of decentralized information gathering toward a simple problem: Retrieved 19 November Archived from the original on 1 June
Even without such a change, ether itself will retain a strong and steady value as a cryptofuel, and as a store of value for Ethereum-based security deposits, simply because of the combination of the Ethereum blockchain's network effect which actually is a platform network effect, as all contracts on the Ethereum blockchain have a common interface and can trivially talk to each other and the weak-currency-network-effect argument described for cryptofuels above preserves for it a stable position. ASIC-Resistant Proof of Work One approach at solving the problem is creating a proof-of-work algorithm based on a type of computation that is very difficult to specialize. Step by step. Hash-Based Cryptography Consensus 6. Choose your language. Additionally, cryptocurrency private keys can be permanently lost from local storage due to malware, data loss or the destruction of the physical media. The most common solution to this problem is punishment - an act which is harmful in itself, but which shifts the incentives so that attacking is no longer beneficial to the perpetrator. Announcing the first release of Bitcoin, a new electronic cash system that uses a peer-to-peer network to prevent double-spending. However, unique non-fungible tokens also exist. Ana Alexandre.
- altcoin mining on old hardware mining diamond coin
- how do i find my old bitcoins quant trading bitcoin
- transfers between epay and coinbase coinbase keeps canceling my order
- litecoin chart all time bitcoin good or bad investment
- see bitcoin transactions live what is bitcoin investment trust
Disclaimer and Confirmation
PPG LEGAL
ADVOCATES & SOLICITORS
Disclaimer & Confirmation
Within the professional code of conducts and applicable ethics and rules & guidelines of the Bar Council of India, Practicing Lawyers are not permitted to solicit work and advertise. The user of this website acknowledges the following:
- The content published here are not to be construed as advertisement, personal communication, solicitation, invitation or inducement of any sort whatsoever from us or any of our members to solicit any work through this website;
- The information read or downloaded from the website is purely a user wishes to gain more information about us for his/her own information, consumption and use;
- The information about us is provided to the user only on his/her specific request.
The information provided under this website is solely available at your request for information purpose only and should not be interpreted as soliciting or advertisement.
PPG Legal and/or its team members are not liable for any consequence of any action taken by the user relying on material/information published under this website. Further the blog post published here are also from various sources of public utility system and/or independent writers. Views published therein necessarily are not ours.
In cases where the user has any legal issues, he/she in all cases must seek independent legal advice, as the material contained in this document is not professional advice that may be required before acting on any matter. While, we do take necessary care in preparing the content of this website and web pages to ensure accuracy at the time of publication and creation, however, PPG Legal and/or its Associates assume no responsibility for any errors, which despite all precautions may be found herein.
All disputes, if any, are subject to the exclusive jurisdiction of courts at New Delhi, India only.
