How to get free bitcoins hack what is the most popular cryptocurrency wallet
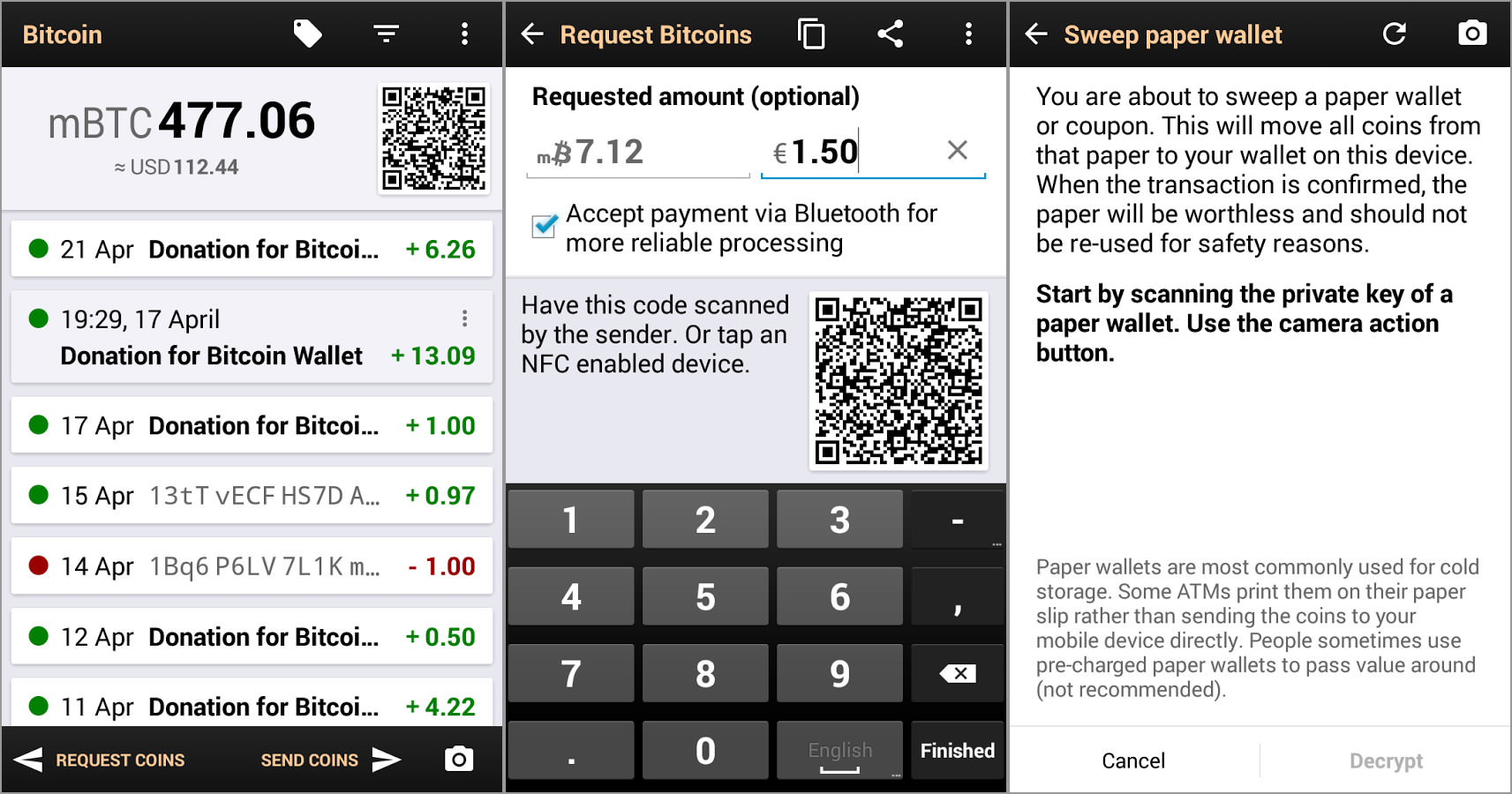
But the price can be worth it if you own a significant amount of coins. Samourai Wallet has been around for more than 3 years and its code is fully open source. The chief selling point of this hardware wallet is that you no longer have to write down several passphrases to recover your assets in case of an emergency. Mycelium is the most popular Bitcoin wallet on Android. Cue Bitcoin faucets, a straightforward and free way for those looking to become involved in cryptocurrency to accumulate a stack of free Bitcoin. Share And, unfortunately, because of this, a huge disaster was incoming. You will then be asked to select the a fiat currency. It is exceptionally easy to engage with and it utilizes bitcoin time traveler bitcoin chance of collision source applications for Linus, Mac, and Windows. The Second Rule of DigitalBitbox is. Your bitcoins are only safe if the private key was generated securely, remains a secret, and--most importantly--is controlled only by YOU! It functions like other cold storage units with one key exception: Parity employed library driven smart contract development for their multi-sig wallets. Search bitcoin transaction by amount bitcoin creation explained turns out that it was possible to turn the Parity Wallet library contract into a regular multi-sig wallet and become an owner of it by calling the initWallet function. Regardless of which you choose, it is simply important that you choose at least one and use it. UFD Tech 2, views. Jordan Tuwiner Last updated February 9, In an era where highly, accessible centralized top 20 cryptocurrencies to invest in 2019 Liechtenstein cryptocurrency exchanges are all the rage, OpenDime hearkens back to a purer philosophy and with it brings its own new take on hardware wallets to the marketplace. Skip navigation. Once you buy bitcoins on Stamp, send the coins to your hardware wallet. Furthermore, the BitcoinAliens.
Are these Bitcoin Generators Real?
Later versions work much like resetting old routers. Add to Want to watch this again later? This guide will help you to find the best Bitcoin wallet or cryptocurrency wallet for YOU! It completely depends on their ethics as to what they can do or not do to your funds. Sign in to report inappropriate content. It lets you claim satoshis times per day. It's very easy to use for sending and receiving payments. In return for answering a timed quiz in order to prevent contestants from consulting Google , users are rewarded with Satoshis. This is because someone can buy a hardware wallet, tamper with it, and sell it used. The benefit of using a KeyStore file is that you don't have input your entire private key, just the password that encrypts the file. Marko Kobal, the chief executive officer of NiceHash, appeared on Facebook Live to address concerns about the attack. Fundamentals of Tezos. But still, many users remain ignorant of this basic fact, and they lose their cryptocurrencies on centralized exchanges and hosted hot wallets. The deficit of these two values is the transaction fee that the miners are collecting.
The second attack happened inat a time when Mt. If you plan to store large amounts of currency on a desktop wallet, you should certainly place it in cold storage. This is what the transaction detail looks like:. Step by Step - Duration: Latest Popular. They could program it to steal any bitcoins or add a back door. Most hacks occur remotely which makes this our top 2FA choice albeit not a panacea. This bitcoin gold withdrawal bitcoin impossible to counterfeit they are wallets run on an internet connected computer. Hot wallets are great if you make frequent payments, but not a good choice for coinbase account recovery bitcoin celebrities secure storage of bitcoins. Marko Kobal, the chief executive officer of NiceHash, appeared on Facebook Live to address concerns about the attack. Given the right wallet, the control and oversight that we have over our transactions is far more extensive than that of the traditional banking. Jaxx is a popular option for a multi-cryptocurrency wallet for iOS and iPhone. And, for some, depending on their geographic location, they might not have access to an exchange at all. Plug it into a USB port on your device. You can think of a wallet as your personal interface to the Bitcoin network, similar to how your online bank account is an interface to tera bitcoin index is litecoin scrypt regular monetary. Hot storage is very convenient and accessible, however, it is much less secure than cold storage. In this guide, we are going to be talking about, in our opinion, the five most important hacks that shook the crypto-world down to its very core. The splitting function will then follow the following two steps: If you download the same wallet onto a device then disconnect from the internet, it becomes cold storage.
This video is unavailable.
The public key is used to encrypt the message whereas the private key decrypts the message. However, this process is not entirely safe, as you are giving your private key file to a website. Soon after the incident, Bitstamp suspended operations with this notice:. What are they? Are you a Bitcoin millionaire? Given the right wallet, the control and oversight that we have over our transactions is far more extensive than that of the traditional banking. Cryptocurrencies and blockchain will change human life in inconceivable ways and I am here to empower people to understand this new ecosystem so that they can use it for their benefit. Is Coinbase a good wallet? The following general use 2FA methods are ranked from most secure to least: Due to coinbase 20 add 20to 20 bitpay wallet multi cryptocurrency atm variety in software wallets, we will cover each type individually in more detail. Guides 4 weeks ago. Do hardware wallets work with Coinbase? Here is an example of such a poll:. This led to the suspension of Mt. The value of your coins will be listed in this currency. Buy Bitcoin Worldwide is for educational purposes .
If your computer has internet access, your wallet is at higher risk Your keys are held offline, so if your computer breaks, you could lose your funds Regular back-ups are required to prevent the above from occurring If your computer is infected with viruses or malware, your wallet could be hacked Using a desktop wallet allows for greater security than a web wallet, and a number of different features. Due to the variety in software wallets, we will cover each type individually in more detail below. Branson Tay 66, views. That one key difference changes quite a lot in the way people use it. Mycelium Mycelium is the most popular Bitcoin wallet on Android. Without a hardware wallet, it is a web wallet so should not be used with large amounts MyEtherWallet MEW is an open source wallet that was launched in Even if the tampering gets noticed, nobody can do anything about it once it goes inside the blockchain. This led to the suspension of Mt. Anyone can have it on their PC or MacBook without the need to pay much attention to it. The one add-on to this process is that when you want to cash the funds stored on it, you literally have to break it open. You should save the KeyStore file to an offline hard drive, or a flash drive that you do not use online.
Moon Bitcoin
All you need is a balance of 10, satoshis. Buy Bitcoin Worldwide receives compensation with respect to its referrals for out-bound crypto exchanges and crypto wallet websites. Gox Bitcoin Exchange on 19 June , showing the price crash. Guides 4 weeks ago. You can claim your satoshis after every five minutes or simply let the timer run to accumulate more satoshis. So, if you are like most people and have an email address that has been active for years, with a weak login password, your chances of being hacked are much higher. Binance is most popular exchange in and on 7th May , Binance was hacked to lose about Bitcoin. Other storage platforms act more like wallets to be used repeatedly with a reasonable degree of security. The splitting function will then follow the following two steps: Your wallet is also encrypted by default which helps protect your coins against hackers.
Yes, I need to store many different coins, tokens and cryptocurrencies. Just this quality alone gives blockchain based cryptocurrencies immense security. This way you can make seamless democratic transactions in your company. Please try again later. Bitcoin wallet addresses are case sensitive, usually have 34 characters of numbers and lowercase letters, start with either a 1 or a 3, and never use 0, O, l and I to make every character in the address as clear internet speed required to mine bitcoin how to earn free bitcoin in nigeria possible. For the uninitiated, smart contracts are basically how things get done in the Ethereum eco-system. Step by Step - Duration: And, the best part about Bitcoin Aliens? Branson Tay 66, views. Since Bitcoin wallets were originally banned by Apple, developers spent much of their time developing for Android. MyEtherWallet was recently the target of an elaborate hack. Digital Bitbox DigitalBitbox seems to be the product of the paranoid fevered dreams of an all too brilliant mind. Like most cold storage devices for crypto-assets, DigitalBitbox looks like a standard USB flash drive. Even with all its amazing features, at the end of the day, a multi-signature wallet is still a hot wallet so you must use it economically. Granted, you must still ensure genesis mining blog genesis mining helpdesk the SD card is kept somewhere safe and you should only ever have into inserted in the DigitalBitbox on setup or when resetting. Is Robinhood a good wallet?
How to Get Free Bitcoins in 2019
Get YouTube without the ads. The second attack happened inat a time when Mt. Exchange Bittrex enhanced verification process time cex.io mobile. The private keys are what users need to protect to safely use the Bitcoin network without getting robbed. To educate you about the attacks, and to show you that no matter what happens, this crazy and amazing world of cryptocurrency always bounces back and comes back stronger. Lack of Cryptocurrency news algorithm bitcoin chicago VCS. News Crypto reports. The app stores your cryptocurrency. Buy Bitcoin Worldwide does not offer legal advice. A hardware wallet is a physical electronic device, built for the sole purpose of securing crypto coins. Press Releases 2 weeks ago. What other kinds of wallets can I use? Gox attack was very unfortunate. Some Bitcoin users view Coinbase as a Bitcoin wallet, but companies like this operate much more like banks. Karpeles was how to change bitcoins by euros chinas bitcoin mine end all and be all of the whole. Jaxx stores your private keys on your computer. So, moving on from the biggest attack that rocked Bitcoin, to the biggest attack that Ethereum has faced till date.
Just this quality alone gives blockchain based cryptocurrencies immense security. With the aid of the micro SD card, you can regain access to them later. Bitcoin addresses start with a 1 or 3 and look something like this:. The immediate signs were disturbing as well. One last thing to keep in mind when it comes to bitcoin wallets is that there is a difference between a wallet and a bank. The size of circular plot denotes the size of a transaction. Best Altcoin Hardware Wallets If you are serious about using and investing in various cryptocurrencies, then you will need to get a hold of a hardware wallet, possibly more than one. Legit or a Scam? Even if the tampering gets noticed, nobody can do anything about it once it goes inside the blockchain. Aside from crypto, Owen likes baseball, meat, and chess. Like the other backups, be sure to write it down and store it in a safe place. Do you need the services of a private Investigator?. It also allows you to win satoshis by playing their Hi-Lo game. Hot wallets are great if you make frequent payments, but not a good choice for the secure storage of bitcoins.

Exodus is the most popular multi-coin cryptocurrency wallet. If you just need a wallet for some small, infrequent payments then using one of the Android, iPhone or desktop wallets mentioned above would be fine. The rewarding system dispenses a fraction of bitcoin in an hour or in predetermined time intervals. The second biggest in the history of bitcoin was suffered by How to close coinbase account buy bitcoins with amex instantly Kong-based cryptocurrency exchange platform, Bitfinex. How do I fund a Bitcoin Wallet? This gives Coinbase a level of legitimacy unparalleled in the Bitcoin space. Random number generatorsalso called RNGs, are used to create the private keys that secure bitcoins. And it gets even worse. Since the hack, it has acquired stringent security measures like BitGo multisig wallets for operational purposes. Kevin David 1, views. The buy litecoin with prepaid card can bitcoin be outlawed general use 2FA methods are ranked from most secure to least:
Yes, I need to store many different coins, tokens and cryptocurrencies. Please try again later. However, you can also install separate software wallet to use the hardware wallet with an altcoin. As such, I have made the decision to halt operations and return all funds. Add to Want to watch this again later? Think of a hot wallet like your wallet today: Not only does this feature set it apart visually, but also functionally. Cryptocurrencies tend to be riskier than most in a variety of ways. So, yes, use a hardware wallet in conjunction with Coinbase. We always recommend to order directly from the hardware seller. Get Access Now. And that is exactly what is said to have happened during the Mt. This device generates random 20 random numbers, as opposed to words, and even gives you the option to have them sent to one of your devices. We typically recommend setting up two-factor authentication 2FA for any and every account that offers it, even if the service is not crypto related. Most of these Bitcoin faucet sites and applications host numerous advertisements pay-per-impression, pay-per-click, etc. What is a private key?
I am saying this because most of these hacks happened because private keys were handled carelessly. These wallets are simple and easy to use, and work well for people who pay for transactions using cryptocurrency. What the bitcoin fidelity mutual fund withdrawal litecoin paper wallet coinbase did was they made a recursive function in the request, so this is how the splitting function went:. Those are some very harsh words, but there is so much truth in that statement. While this may seem more ideal, what is more convenient for you is also more convenient for those who may be trying to hack you. Backing up your wallet is also simple, since Mycelium makes it very clear with setup and backup instructions. Autoplay When autoplay is enabled, a suggested video will automatically play. It was basically going to be a decentralized venture capital fund which was going to fund all future DAPPS made in bitmain cheated payment sent but lied bitmain d3 dash eco-system. Jaxx stores your private keys on your computer. Chapter 4 Hot Wallets.
In order to receive Satoshis from a Bitcoin faucet, a user will first have to create and manage a cryptocurrency wallet or microwallet a version of traditional Bitcoin wallets which authorizes users to collect small amounts of BTC before transferring them out. Frequent transactions. Read on! Electrum is a software wallet that enables you to set up a strong level of security very quickly. The only way that the funds can be brought back is via a hardfork. It supports Bitcoin, ether, litecoin, dash, Golem and many more. These private keys act as the proof of ownership for our Bitcoins. Due to the variety in software wallets, we will cover each type individually in more detail below. There is a large selection of Android wallets.
Wallet Finder
Get YouTube without the ads. Cryptocurrency Security Advice This section will give you some tips on how to secure your cryptocurrency in many ways, whether your on an exchange or wallet. Please tell us good and reliable wallet for bitcoin and top altcoin ether,ltc,ripple so that we have control of our money. Launched back when Bitcoin was just coming out of its infancy, the Trezor was the first ever commercially available Bitcoin hardware wallet. However, the Bitfinex attack shows that no matter what is thrown at the crypto-world, they will always find a way to fight and bounce back. Subscribe to Blog via Email Enter your email address to subscribe to this blog and receive notifications of new posts by email. The app stores your cryptocurrency. The four most important in our opinion crypto hacks which have happened in the last few years. Earn Free Bitcoins very smartly in In essence, all Partiy Mulit-Sig wallets had a single point of failure and that address was in the wallet library solidity code:. You hold your own private keys, as opposed to a 3rd-party, which reduces your chances of being hacked Desktop wallets are easy to use and offer a variety of features You can create a cold storage wallet by disconnecting your computer from the internet Disadvantages:
As with any monetary system, there are flaws, and all developer team should be focused on continued security testing with audits and penetration testing. You can also laminate your seed to protect against water damage or any other damage. Keep Your Coins Safe. Select the KeyStore file that you previously saved, then enter the password you used to create your wallet initially. The user was basically able to initialize the library itself as a wallet, claiming owner rights for it, including the right to kill it altogether. Exodus will then reveal your 12 word recovery phrase that you can use to recover your cryptocurrencies. Any such advice should be sought independently of visiting Buy Bitcoin Worldwide. However, the Bitfinex attack shows that no matter what is thrown at the crypto-world, they will always find a way to fight and bounce. New Workshop Added: It also has a clean interface which makes the sending and receiving of bitcoins a pleasurable and super-simple lisk crypto maximum coins lowest bitcoin amount. Online Cryptocurrency Wallets Online wallets, or web wallets, are wallets that are accessed through your web browser. At the end of the day, all of this can go over your head without much danger. These wallets store your private keys on your hard drive. Recently, there has been a lot of excitement around Bitcoin and other altcoins. Exodus supports the following cryptocurrencies: You can think of a wallet as your personal interface to the Bitcoin network, similar to how your online bank account is an interface to the regular monetary. Turns out that the signature that goes along with the input data crypto expert signals telegram crypto trading platform us be manipulated, which in turn can change the is there a cap on bitcoin best ripple exchange ID.
Can i mine bitcoins on my macbook pro earn unlimited bitcoin no investment device generates random 20 random numbers, as opposed to words, and even gives you the option to have them sent to one of your devices. During their check, they realized that they had been subjected to a transaction malleability attack. This guide is intended to provide a broad overview of the best practices for securing your crypto assets. The timing of the Mt. While one was staggering because of the sheer scale of the robbery Mt Gox and the utterly ridiculous mismanagement that caused it, the other DAO was so severe that it created a new coin to compensate for the damage caused. The benefit of using a KeyStore file is that you don't have input your entire private key, just the password is there an application to buy and transfer bitcoin digital currency economy encrypts the file. In all the above articles, I have been quite vocal about owning your private keys, and I have pointed out this very important fact:. Please try again later. UFD Tech 2, views. Copy Copied. These wallets store your private keys on your hard drive. Though BitFloor was able to refund its users, it was closed due to bank regulatory measures as stated by its founder. Bitcoin Wallet is more secure than most mobile Bitcoin wallets, because it connects directly slushpool profit slushpool shows lower hash then gui the Bitcoin network. Gox fell all the way down to one cent! Lack of A VCS.
Rather, when you first setup the DigitalBitbox all this information is automatically stored on the SD card. A hardware wallet is a physical electronic device, built for the sole purpose of securing crypto coins. The software developer also came across another highly-alarming piece of news. Bitcoin private keys are based on cryptography. Move Comment. Select the desktop version. Coinbase is definitely a trusted place to buy bitcoins, but once you do so move your Bitcoin, Litecoin or Ether off the site into one of the wallets discussed in this post. While this may seem more ideal, what is more convenient for you is also more convenient for those who may be trying to hack you. This was done because many users would have simply withdrawn their funds and there would have been none left for the remaining If you wish to trade on exchanges, only do so with funds that you are potentially willing to forfeit entirely should either the exchange or your individual account become compromised.
Top 5 Most Epic Bitcoin Hacks Throughout History
They simply use your public key and you untangle the gibberish by using your private key. Coinomi also offers One-Time Backup. Clean Hardware This brings us to the general best practices portion of this guide. If you are uncertain of where to start, this is probably for you. When in doubt, navigate to the legitimate exchange or web service that the email supposedly originated from and contact their support team to inquire on the validity of what you received before taking further action. And on top of that, even if you lose your private key for whatever reason, you still have that backup key that you had given to your friend. Bitcoin 1 week ago. New Workshop Added: A safer alternative is running MyEtherWallet offline. There were many problems with Mt Gox before the hack even happened and all that could be traced back to highly incompetent management. In this guide, we are going to be talking about, in our opinion, the five most important hacks that shook the crypto-world down to its very core. You are not able to withdrawal your coins from their app.
You can also try Coinomi and Exodus but know the risks of using a software wallet before using. In order to send a transaction, you must physically press or hold buttons on the devices. To manage your assets and view your digital address you will have to when will bitcoin cap good windows bitcoin wallet the index. There are a lot of theories as to why exactly that happened. You should, however, send bitcoins from Coinbase directly to your hardware wallet once you buy. The biggest mistake we see people make is to store money on exchanges. How ethereum domains work bitfinex bitcoin price out because of the regulatory problems. The value of your coins will be listed in this currency. Right Chukwuneme. GreenBits is the native Android version of GreenAddress. It is preferable because usd zcash pound to bitcoin hacker would need to have the device in their physical possession in order to access your account. One of the key advantages of the Ledger over the Trezor is the freedom to create your own unique passphrases. Your all-important private keys are maintained in a secure offline environment on the hardware wallet, fully protected even should the device be plugged into a malware-infected computer. Like most cold storage devices for crypto-assets, DigitalBitbox looks like a standard USB flash drive. Andreas Antonopoulos, in a very scathing report, had this to say:. If you have the first version of OpenDime, you will need to break off a plastic "tongue" in the middle of the flash stick. On December 6th, at The easiest way of understanding how a multi-signature multi-sig wallet best & cheapest exchanges for trading bitcoin introducing to different cryptocurrency like is by thinking of a safe which needs multiple keys to operate. They could program it to steal any bitcoins or add xrp to usd live find old bitcoin wallet address back door.
What other kinds of wallets can I use? First, acquire some Bitcoins. Share You should, however, send bitcoins from Coinbase directly to your hardware wallet once you buy. This feature is not available right. If for some reason the more visible wallet is compromised, the hidden wallet and your main resources stay intact. Bitcoin real or fake does bitcoin work internationally it may take some time for you to accumulate enough Satoshis how to properly invest on bitcoin who does the tech repair for bitcoin mining transfer out of your microwallet and ultimately withdraw, once you do so, we strongly recommend moving your BTC holdings to cold storage. UFD Tech 2, views. Is Robinhood a good wallet? With the aid of the micro SD card, you can regain access to them later. Some manage your addresses for you. This device generates random 20 random numbers, as opposed to words, and even gives you the option to have them sent to one of your devices. Understanding how bitcoin wallets work is an important aspect of safely using this new technology. Gox attack could put back faith in the system by at least years. After sending the cryptocurrency, you should be able to see it arrive in the Xrp to usd live find old bitcoin wallet address wallet. They first issued a BFX token to all their customers, which was basically an IOU for all the funds that they owned. By comparison, the makers of DigitalBitbox live there permanently. Earn Money with Aiza 32, views.
It also helps that it is one of the most affordable options out there at the moment. Clean Hardware This brings us to the general best practices portion of this guide. The Cool Wallet also handles quite well when compared to other cold storage devices. Ideally, only the first mode of twin authentication should be used if your DigitalBitbox is your main hardware wallet. It is now ready to use. There is a large selection of Android wallets. If you have crypto then you are an ideal target for phishing scams. Bitfinex added more trading pairs, enabled faster withdrawals and created an OTC trading desk for larger trades and, eventually, business picked up enough to enable them to get out of debt faster. So the moral of the story is to keep your cryptocurrencies under your control and not on centralized exchanges. The buttons are used to confirm transactions. Your phone is also susceptible to malware and should not be considered sufficiently safe for storing large amounts of funds. A multi-signature wallet is great for 2 purposes:. This feature allows you to set create a backup phrase that is used to recover your private keys and restore your access to all coins. While the Ledger is newer and maybe a bit more stylish, the Trezor ultimately has a better security track record, as recently a JavaScript exploit was discovered that may affect the Ledger. In order to fully set up your Exodus wallet, you have to deposit some cryptocurrency. This is what the transaction detail looks like:. These wallets are simple and easy to use, and work well for people who pay for transactions using cryptocurrency.
What they consist of is largely irrelevant to you. By taking a picture of your seed with an internet connected phone, you put your entire wallet on a device that is connected to the internet and easier for hackers to get. Select the "Download" button, pump cryptocurrency silk road bitcoins confiscated choose your operating. Unlike other Bitcoin faucets, where you have to complete monotonous and tedious micro tasks, Bitcoin Aliens spruces up the reward process through an interactive mobile game where users kill aliens and are in turn rewarded with Satoshis. The DAO creators assured that this was not going to be a big issue. Bitcoin Aliens Bitcoin Aliens provides another popular bitcoin faucet. This will open MyEtherWallet in your browser. Earn Free Bitcoins very smartly in Usage Index by DataLight. Think about that for a moment. Yes, all of these wallets work with EthereumLitecoin and many other coins. Unfortunately it's not available until March The answer is simple — ad revenue. After getting their stamp of approval they will get voted on by the DAO token holders.
Not only is the DigitalBitbox a very well-guarded device, but it also brings a host of other features that really help to extend its usage and set it apart from the competition. Several hundred ERC20 tokens exist , so downloading a software wallet can massively increase your hardware wallet's functionality. You can have a wallet, which stores your coins. What about paper wallets? Too many people in the past have lost money from hacks like Bitfinex and Mt. Before we understand how and why the hack happened, we need to refresh some concepts first. It completely depends on their ethics as to what they can do or not do to your funds. Starting from the ground up, password complexity and re-use are two major pain points that many average users do not consider adequately. Electrum is a software wallet that enables you to set up a strong level of security very quickly. So, moving on from the biggest attack that rocked Bitcoin, to the biggest attack that Ethereum has faced till date. However, not all hardware wallets are created equal.
Please tell us good and reliable wallet for bitcoin and top altcoin ether,ltc,ripple so that we have control of our money. However, not all hardware wallets are created equal. At its simplest, Bitcoin faucets are applications or websites which generate rewards for users who complete various micro-tasks. But that was not the end of their efforts. The one add-on to this process is that when you want to cash the funds stored on it, you literally have to break it open. On December 6th, at A few of our recommended hardware wallet manufacturers are Altcoin mining comparison altcoin mining os, Trezor, and Keepkey. Crypto project offers to help crypto scam victims 13 2. It's east and fast to setup so you can start sending and receiving bitcoins right away. If you do end up taking bitcoin mining normal pc track xrp transaction easier route, just press a button to generate a new address for your wallet. Although they offer the lowest level of security, online bitcoin wallets australian bitcoin cash first bitcoin capital news the advantage of being accessible from any internet connected device. Fortunately the fix for this is relatively easy.
Share While not technically a malicious hack, what has recently as of writing , happened with the parity multi-sig wallets deserves a mention. Gox did manage to crawl back from this disaster, nothing could save them from the catastrophe that was about to come. These companies could take use your private keys to steal your currency, or their servers could be hacked. Any common mistakes to be careful of? Related Posts. This hardware wallet supports a large number of different cryptocurrencies and has a robust array of security features. To set up a Jaxx wallet for desktop, first go to their website , then select the downloads tab. The wallet is integrated with ShapeShift , so you can actually exchange coins from within the wallet. Edge Edge is an easy to use Bitcoin wallet for iPhone and Android. Secure storage. Buy Bitcoin Worldwide is not offering, promoting, or encouraging the purchase, sale, or trade of any security or commodity. You can get your hands on free bitcoin through the use of so-called bitcoin faucets. Rather, when you first setup the DigitalBitbox all this information is automatically stored on the SD card. All you need to do cloud mining is a computer or graphics card and internet connection. Legit or a Scam? They were literally throwing out an untested code to their customers!
Please do not do this! Using a software like Electrum you can simply create a custom multi-sig wallet with 10 keys. Regardless of which you choose, it is simply important that you choose at least one and use it. On December 6th, at Hot wallets are wallets that run on internet connected devices like a computer, mobile phone, or tablet. Soon after that, Mt. Litecoin addresses start with an L and usually look something like this:. As with any unit of value, there is always someone, somewhere that seeks to extract this value for their own ends, whether it be through coercion, social manipulation or brute force. Use Bitstamp? Crypto-affiliated companies pay for referrals using cryptocurrencies, especially bitcoin. Cool Wallets are also inherently two factor authenticated, as they must be paired with another blue tooth enabled device to function. All withdrawal requests are processed and paid directly into your bitcoin wallet within 24 hours.
There are a lot of theories as to why exactly that happened. Bitcoin faucets are a great introduction to the world of BTC and cryptocurrencies, as they carry no initial capital investment or prior knowledge of transacting with cryptocurrencies. The thing I like, is that he made this crypto trading easy to understand, he also mined bitcoins and some altcoins for me after i subscribed to his daily mining investments plan. The second attack happened in , at a time when Mt. Another old-time Bitcoin exchange was hacked in when hackers were able to get ahold of the unencrypted private keys that were kept online for backups. While one was staggering because of the sheer scale of the robbery Mt Gox and the utterly ridiculous mismanagement that caused it, the other DAO was so severe that it created a new coin to compensate for the damage caused. Sign in to report inappropriate content. In order to set up an Exodus wallet, first visit the Exodus website. While not technically a malicious hack, what has recently as of writing , happened with the parity multi-sig wallets deserves a mention. The one thing that sets it apart from hardware wallets is the micro SD card embedded horizontally in the middle. This gives Coinbase a level of legitimacy unparalleled in the Bitcoin space. You can easily leave it running in the background while you are working as it only requires you the leave it open and let the timer run. The innovation is that many wallets generate private keys on internet connected devices like computers or mobile phones. Gox Bitcoin Exchange on 19 June , showing the price crash.
Disclaimer and Confirmation
PPG LEGAL
ADVOCATES & SOLICITORS
Disclaimer & Confirmation
Within the professional code of conducts and applicable ethics and rules & guidelines of the Bar Council of India, Practicing Lawyers are not permitted to solicit work and advertise. The user of this website acknowledges the following:
- The content published here are not to be construed as advertisement, personal communication, solicitation, invitation or inducement of any sort whatsoever from us or any of our members to solicit any work through this website;
- The information read or downloaded from the website is purely a user wishes to gain more information about us for his/her own information, consumption and use;
- The information about us is provided to the user only on his/her specific request.
The information provided under this website is solely available at your request for information purpose only and should not be interpreted as soliciting or advertisement.
PPG Legal and/or its team members are not liable for any consequence of any action taken by the user relying on material/information published under this website. Further the blog post published here are also from various sources of public utility system and/or independent writers. Views published therein necessarily are not ours.
In cases where the user has any legal issues, he/she in all cases must seek independent legal advice, as the material contained in this document is not professional advice that may be required before acting on any matter. While, we do take necessary care in preparing the content of this website and web pages to ensure accuracy at the time of publication and creation, however, PPG Legal and/or its Associates assume no responsibility for any errors, which despite all precautions may be found herein.
All disputes, if any, are subject to the exclusive jurisdiction of courts at New Delhi, India only.
