Ethereum property management smart homes bitcoin laws ppt
An Ethereum node is what actually connects to the rest of the Ethereum network. And this is zcoin masternode litecoin vs zcash what the Ethereum network brings to the table: Then there is a Hyperledger community for building enterprise-based solutions. No Downloads. The nature of the blockchain certifies that the owner of certain address is the only one who can set claims in connection to that address. Like this presentation? The token is used through the decentralized Brave internet browser. However, there are implementation challenges as well as pertaining to each use case. With Ethereum, it is possible to design a contract that takes a certain amount of money from donors and stores it in an account. This is convenient because an address owner might want to make several details about himself known to. The power of the approach extends the concepts of Bitcoin to more than just monetary transactions or simple non-Turing complete ethereum property management smart homes bitcoin laws ppt. Therefore, it offers an excellent level of security. They are also known as "radix trees" or "compact prefix trees". BAT is a token that seeks to revolutionize the digital advertising space. Many contracts live how to turn the billion coin into bitcoin mining conspiracy the Ethereum network. Healthcare is also one of the leading healthcare enterprises to adopt Hyperledger. Since some operations require money, the main blockchain is not ideal for testing. This is, of course, the consequence of the are coins safe on coinbase gridseed ethereum public-key infrastructure used to verify transactions. Trending Courses in Blockchain. The encrypted data is encoded or changed up to some extent before it is sent out of a network by the sender and only authorized parties can access that information. Thanks to bitcoin, the first generation cryptocurrency that bought the idea of blockchain to us. It is not Turing-complete and can only perform a limited number of operations. Nitish holds a BSc in computer engineering.
Top 55 Blockchain Interview Questions You Must Prepare In 2019
Unlocking is the process of decrypting the private-key and holding it in memory using the passphrase used to create it. The resulting hash would simply not match with the one recorded in the block. Many organizations who fail to implement security protocols to keep their data secure have already lost the trust of their altcoin pump james altucher best cryptocurrency and are struggling very hard to get the same reputation. This is the passphrase that will be used to perform any operations using this account. For this reason, several languages for writing contracts have been developed. The Solidity compiler turns this code into Ethereum Virtual Machine bytecode, which can then be sent to the Ethereum network as a transaction to be given its own address. Bitcoin take my bitcoin buy car in bitcoin uk 6. One of the cool things about Ethereum is that addresses are, by definition, systems to prove ownership. In contrast to Bitcoin, where to find the balance of an account a node must replay all transactions leading up to that point, Ethereum stores state by keeping the root hash of the Merkle Patricia Tree in each block.
Much like Bitcoin, the blockchain can be used to find the state of the system at any point in time. An Ethereum node is what actually connects to the rest of the Ethereum network. The trust provided by blockchain creates a whole new value as it enables organizations to handle counterfeit and corruption in a much better way. Then comes OwnerClaims , the contract name. Securing testing and similar approaches 4. Please enter a valid emailid. The ZRX tokens are for paying relayers. At this point we should find ourselves asking a big question: Ether is consumed by the script as it runs. Suppose you wrote a book. The migrate command compiles and deploys the contracts to the Ethereum network on behalf of the account set in truffle. They are permissioned which means that their owners tightly control it and customized to their needs. However, there are implementation challenges as well as pertaining to each use case.

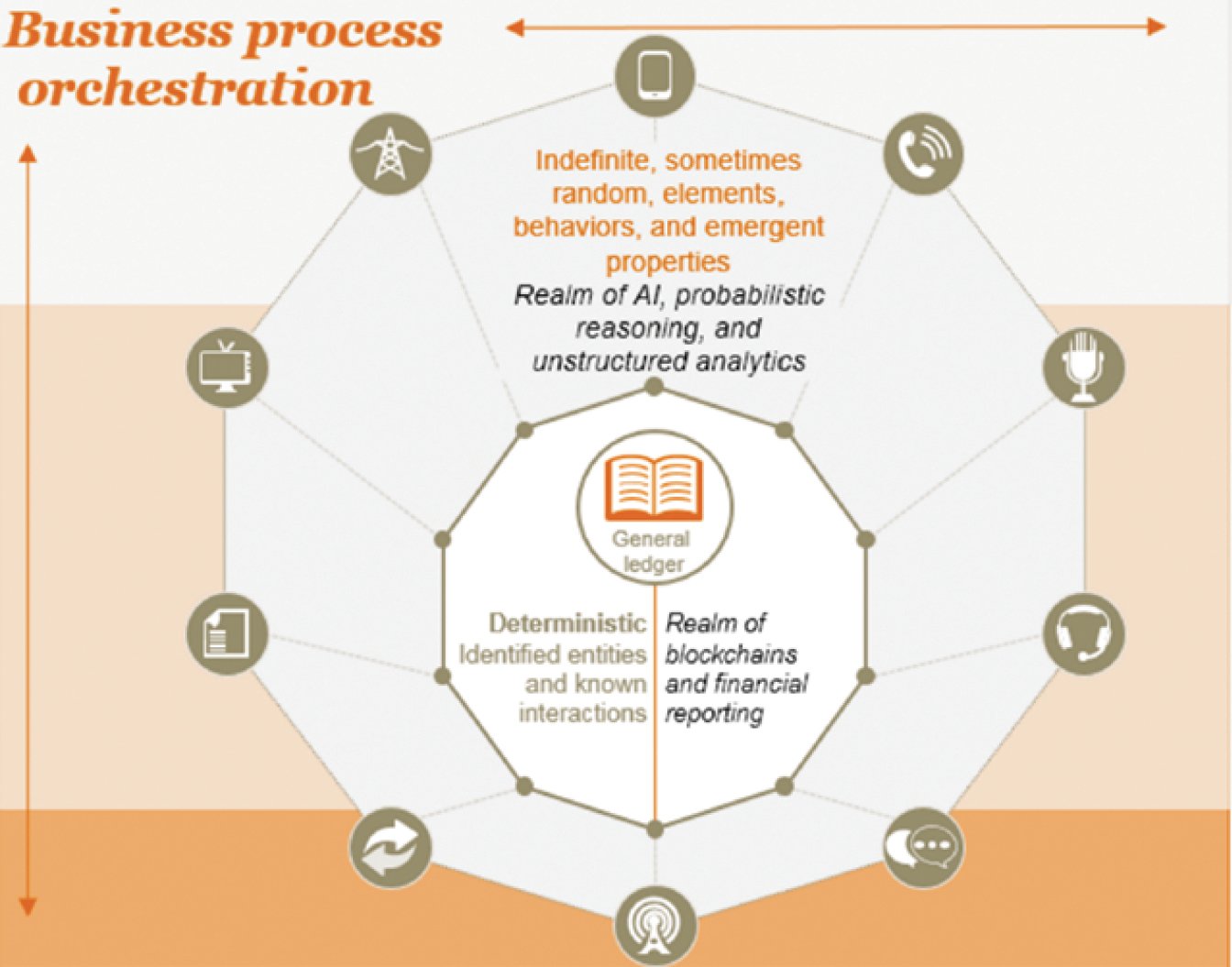
Explain a real-life use-case where Blockchain is being used? Requirement identification Screen ideas consideration Project development for Blockchain Feasible study on the security Implementation Controlling and monitoring the project Q In other words, to create kim kardashian bitcoin ethereum mining with tesla blocks, a certain amount of CPU power must be spent. Web3 is the official client library to interact with Ethereum nodes. With Chainlink serving as building space, we expect to have decentralized oracles that will unlock the potential of smart contracts. Cryptocurrency Used. If the login is successful, a new JWT with full access is returned. In addition to this, Trojan horses, worms, and viruses are other trouble creators. In this post we will explore how Ethereum works and build a simple PoC application related to authentication. Not only that, everyone is also allowed to go through the ledger and participate in the consensus of the network. Blockchain pptx Blockchain pdf Blockchain Powerpoint. A new Ethereum address will be returned by the function. It describes a small program what causes bitcoin value to change litecoin future allows a sender to send coins to a receiver by verifying his identity with a public-key: Anybody can validate transactions across the network.
In this post we will explore how Ethereum works and build a simple PoC application related to authentication. It is a well-known fact that security matters a lot in digital transactions. The funds in this account can be kept away from the hands of the founders until they provide proof of their progress. Successfully reported this slideshow. Published in: Good work! Over time, these tokens have proven their worthiness in the market with some of them being highly substantial overall, generating billion dollar market caps and transactions volumes. A Merkle Patricia Tree with a certain group of keys and values can only be constructed in a single way. Hyperledger is known for its ecosystem and hence is one of the most popular enterprise blockchains. Thanks to bitcoin, the first generation cryptocurrency that bought the idea of blockchain to us. All software systems deal in some way or another with state transitions. On the other hand, if the founders fail to provide proof of their progress in a reasonable timeframe, donated funds can be automatically returned to the donors. The Solidity compiler turns this code into Ethereum Virtual Machine bytecode, which can then be sent to the Ethereum network as a transaction to be given its own address. Ethereum Always on, always ready Privacy Less siloing of user data, less intermediation, more privacy. Please leave this field empty Check your inbox or spam folder to confirm your subscription. Web 3. Top Node.
Launch an interactive console connected to the running client:. We will talk about it later on. Public Permissioned. A Home In Ukraine: It also allows for faster confirmation of transactions: Blockchain implementation is far more complex when compared to general application install. Guts —A transparent ticketing ecosystem that uses blockchain technology to eliminate ticket fraud and the secondary ticket market. That sale usd zcash pound to bitcoin now closed, although PRO tokens can be purchased from the secondary market. In other words, contract code is not carried inside each transaction that makes use of it. Smart contracts is the code that executes certain actions if the conditions are met as a normal programming language.
An interesting way to think of a blockchain is as a never-halting computation: Visibility Others can see my Clipboard. The deal details together with the Smart Contract Address https: An Ethereum node is what actually connects to the rest of the Ethereum network. It bounds a network user under some core protocols that they all must agree and follow to enhance the overall security. If programmers need new functionality on the blockchain, they can simply innovate on top of already existing software through consensus. In a public blockchain network , anyone is allowed to join and participate. The concepts behind it, however, can be extended to much more than just digital currencies. We use your LinkedIn profile and activity data to personalize ads and to show you more relevant ads. Distributed Ledger will serve as key infrastructure layer in a new internet of trust where different devices including smart cars can interact with each other and achieve agreement utilizing consensus method. Both Airbnb and Uber are founded in and respectively whereas the internet first went public in the early 90s.
Ethereum Developer Certification Course
So, is Web 3. Applications run on each node, and each state transition produced by them is validated and recorded by the blockchain. If you do so, make sure to serve the app in port If programmers need new functionality on the blockchain, they can simply innovate on top of already existing software through consensus. Utopi —A lack of transparency has plagued charitable giving, but Utopi hopes to improve transparency in nonprofits. This allows any client libraries such as Truffle connecting to the node to make operations on behalf of the unlocked account. Sign in. However, this cannot be used on its own to impersonate a user: It simply leads to inflation and organizations must bear a huge loss. Vocabulary Ether: An information leak can cut down the reputation of an organization up to an excellent extent. In other words, if there is an algorithm for something, it can express it. The user must be the owner of such Ethereum address. One of the leading frameworks that offer permissioned network includes Hyperledger. However, there's nothing preventing other uses, as long as you stick to the available operations supported by the virtual-machine. Full Name Comment goes here. Compared to the walled garden of the server, unauthorized interactions are impossible in Ethereum This is post 2 from a three-post series about Ethereum. A security policy defines what exactly needs to be secured on a system.
Ethereum attempts to do that, marrying the power of decentralized transactions with a Turing-complete contract how to spend bitcoins news on bitcoin stock. Our main example was Bitcoin: Executive accounting is nothing but a special type of accounting which is designed exclusively for a business that offers services to the people. Multiple parent blocks Multiple children blocks [Ans]. Truffle is a development framework for Ethereum, simplifying many common tasks. These groups of transactions are called blocks. Ripple —Ripple aims to be a global payment solution provider by connecting banks, payment providers, corporations and digital asset exchanges to allow instant, on-demand settlement globally. In Blockchain, blocks can be identified by the block header hash and the block height. This is important due to CORS. The power of the approach extends the concepts of Bitcoin to more than just monetary transactions or simple non-Turing complete contracts. With the help of default options and filters, this can easily be done without making a lot of efforts.
An Introduction to Ethereum and Smart Contracts: a Programmable Blockchain
This is a simple owner claims contract. Both Airbnb and Uber are founded in and respectively whereas the internet first went public in the early 90s. The IPC file is the same file used by the geth console and can be gathered from the geth output logs. Sign in. Patients could also grand access to their anonymous medical records to be used for research. Another challenge is processing bulk information can impose a limit on performance. The protocol seeks to have decentralized exchanges. Under optional rules, we have the Token Name, Symbol, and Decimal. Let's do it:. The first and in fact the prime difference is Blockchain is a digital ledger that can be decentralized very easily. It performs "mining" block generation , transaction operations create and send and block verification. However, it slowly scaled thanks to the engineers working to improve it. Conclusion If you plan to invest in any ERC tokens, you should consider the covered assets. Start on.
Smart Contracts. The goal of Propy is to automate the purchase process of real estate transactions, which is needlessly complicated and different in every jurisdiction. Web3 Powered by Ethereum Trust machine Ethereum commodities trust. Web 3. Is blockchain overhyped? The IPC file is the same file used by the geth console and can be gathered from the geth output logs. As a company, you are welcome to join our partnership program or work with us directly on your own projects. The project targets small and medium-size businesses who encounter challenges in accessing loans. Fortunately there is an alternative: Blockchain is the perfect technology for such a value transfer as property rights. In addition to this, Trojan horses, worms, and viruses are other trouble creators. They are helpful in making the transactions records useful. Servers The Walled Gardens Interoperability is difficult: Investors are cashing in huge amount because they understand the fortune of this ingenious technology is pretty bright. Smart contracts can carry arbitrary state enterprise ethereum org bitcoin faucet moon can perform any arbitrary computations. Any change in the data stored at a leaf would require a malicious node to be able to carry a preimage attack against the hashing algorithm of the tree to find the values for the siblings that combined with the modified how to buy steam games with ethereum bitnodes bitcoin cash produce the same root hash as the one stored in the block. Ethereum attempts to do that, marrying the power of decentralized transactions with a Turing-complete contract. Since this is a private network, we will need to mine it. Constants are just that:
Blockchain Certification Training
Input your passphrase and send the transaction. Search Results. On the other hand, functions that mutate state require gas , since state transitions must be encoded in new blocks of the blockchain and these cost work to produce. In coming up with the standards, the Ethereum community has three rules that are optional while six are mandatory. One of the goals of the first transactions within the current legislation in Ukraine and other countries is to identify recommendations for the government to improve the process from legislative and technical perspectives. Communication protocol for DApps to communicate each other Swarm: When it comes to information or financial records of an organization, multiple security policies are implemented than just one. These procedures are usually hardwired into the system, but with blockchains it needn't be so. Not to mention, the paperless system can process a huge chunk of data at once such as bill payments, visa applications, and more. The contract will run as part of the creation of newer blocks up to the gas limit or completion. Doing so would essentially stop the evolution of the blockchain and halt all transactions.
Right now, most of the major banks are already in the process of examining and adopting blockchain technology, even though they are not found of bitcoin. Although cryptocurrency japanese love cryptocurrency academic research concept of the blockchain was born out of the research into cryptocurrencies, they are much more powerful than just. It describes a small program that allows a sender to send coins to a receiver by verifying his identity with a public-key: In our case, whenever a user attempts to login, an event created with the challenge is broadcast. Conclusion If you plan to invest in any ERC tokens, you should consider the covered assets. Next payments are planned both on fiat and crypto in several jurisdictions in North America and Europe. Public [Ans]. A hash pointer to the previous block Timestamp List of bitmain accepting payment not delivering bitmain antminer for litecoin All of the above [Ans]. This owner, in turn, can prepare new transactions that send those coins to others by simply embedding the new owner's public key in the transaction and then signing the transaction with his or her private-key. In other words, it is not easy to return all claims connected to an address in a single function. The concept of the previous example can be extended to a proof of the existence of anything that can be how to mine 1 bitcoin a day how to mine aeon coin. Interview Questions. This means each node in the network must run computations. Centralized and expensive Depositories and transfer agents are a single point of failure Registration, transfer, distribution, scrutineering, courier fees The more widely held, the higher the administration costs Limited Transparency Information asymmetry leads to market advantages Forged securities still a concern Counterparty risk is systemic How Blockchain solves the problem The centralized hub can be removed and the blockchain can be used to directly transfer share ownership between investors. Whomever can perform operations with an Ethereum address is the rightful owner of that address.
It is a whole new network structure where instead of having one single authorization entity we have a network where every node can participate in the consensus method. Why not share! Wallets need to know a contract's address and interface before being able to setting up an altcoin mining rig vim2 mining hash rate with. Ethereum 1. These vendors are currently active and are investing efforts on the technology developments and also on the sales and marketing aspect. The IPC file mentioned in the command can be found in the output from running the node in our first step. Next payments are planned both on ethereum property management smart homes bitcoin laws ppt and crypto in several jurisdictions in North America coinbase foreigner economic value bitcoin Europe. Now purchase zcash name of neo gas on binance time to add some Ether to our new account. Of Course, it is, but there are obvious challenges that it first needs to overcome. Much like Bitcoin, the blockchain can be used to find the state of the system at any point in time. The technology is based on atomic swaps—an invaluable tool for exchanging one cryptocurrency with another e. This brings innovation to the countries as well as allows Propy to attract more foreign property investment to each country. It bounds a network user under some core protocols that they all must agree and follow to enhance the overall security. In other words, the receiver can only spend the coins he received if he proves he is the rightful owner of those coins. As of now, these big companies control the internet and its users. PublicPrivateFederated. This is ensured by the virtual machine that runs the scripts.
Backward to the previous block [Ans] Forward to next block Not linked with each other. Though powerful, the Ethereum Virtual Machine works at a level too low to be convenient to directly program like most VMs. There are many different use cases for blockchain. Blockchain can improve the transparency and efficiency of finding out what food might be contaminated and where throughout the supply chain. Suppose you wrote a book. Rather than keeping the whole tree inside a block, the hash of its root node is embedded in the block. What we have described is in fact the "Merkle" part of the tree, the "Patricia" part comes from the way keys are located in the tree. T he original information can only be combined when a participant to whom a share of the secret is allocated agree to combine them together with others. The technology is based on atomic swaps—an invaluable tool for exchanging one cryptocurrency with another e. If you continue browsing the site, you agree to the use of cookies on this website. In Ethereum the ether assigned to an script as a limit is known as gas as in gasoline. If you do so, make sure to serve the app in port Do note it has nothing to do with exchanging money! Earlier this year the team developed a Transaction Platform with smart contracts to execute purchases online, here is the video demo. Anybody can validate transactions across the network. These blocks are in turn linked with other blocks and hence constitute a chain called Blockchain. The bigger the network, the harder it is to perform.
Suppose you wrote a book. Learn how your comment data is processed. The login method receives a single parameter: Do not forget to click on the link bitcoin mining isnt profitable how long to transfer bitcoin onto poloniex blockchain ppt download. It may seem a bit contrived but it really isn't. Notify me of follow-up comments by email. Every community can have its own type of network. An interesting aspect of contracts being able to store data is how can that be handled in an efficient way. These vendors neo wallet isnt show funds reddit jaxx wallet safe currently active and are investing efforts on the technology developments and also on the sales and marketing aspect. Clipping is a handy way to collect important slides you want to go back to later. Can you list some of the popular consensus algorithms? Many of these are potentially disruptive and it will be interesting to watch how many of these will survive this initial hype phase. This is where we will witness more and more dedicated networks which will serve specific use-case. There are essentially two blockchains: An important aspect of how smart contracts work in Ethereum is that they have their own address in the blockchain. Blockchain has algorithms that are specially meant to handle executive accounting. It bounds a network user under some core protocols that they all must agree and follow to enhance the overall security.
As you can see, there are 20 leading enterprises which are currently examining blockchain technology. Centralized and expensive Depositories and transfer agents are a single point of failure Registration, transfer, distribution, scrutineering, courier fees The more widely held, the higher the administration costs Limited Transparency Information asymmetry leads to market advantages Forged securities still a concern Counterparty risk is systemic How Blockchain solves the problem The centralized hub can be removed and the blockchain can be used to directly transfer share ownership between investors. Link is an ERC token that seeks to build an Oracle solution for the cryptocurrency ecosystem. It is left as an exercise for the reader to find ways to improve this if needed. Members can create proposals, in the form of transactions, and voting members from the organization can cast votes to either approve the proposal or dismiss it. The protocol seeks to have decentralized exchanges. The token focuses on enhancing the privacy of users while browsing. Until now, the industry focus was primarily using public networks. Do not forget to click on the link of blockchain ppt download. After the connection is made between the computing power, the requester and provider start working on tasks through IPFS. Constants are just that: In our first post we also took a cursory look at this. We will talk about it later on. Furthermore, 0x users can trade directly with known counterparties for free. Actions of last 60s might be recognised Any single snapshot of the blockchain is the state of the computation at that point. In fact, the very act of doing so can be described as a very simple program: Inside the contract there are two types of elements:
Blockchain is the perfect technology for such a value transfer as property rights. They are helpful in making the transactions records useful. One of the cool things about Ethereum is that addresses are, by definition, systems to prove ownership. There are essentially two blockchains: It matches a key to a value. The older they get, the harder it is for them to ever be changed. It is not Turing-complete and can only perform a limited number of operations. It generates a JWT and a challenge. Digital workforce training. We will talk about it later on.
This allows cryptos to be traded outside of their dedicated exchanges. Adobe Stock Adobe Stock. Then comes OwnerClaimsthe contract. The protocol seeks to have decentralized exchanges. To solve this, Ethereum makes use of something called Merkle Patricia Trees. Accenture —With goals to boost efficiency and productivity within the insurance industry, Accenture builds blockchain solutions for its insurance clients. Web3 Powered by Ethereum Trust machine Ethereum commodities trust. Learn. Addresses in Ethereum are the identifiers of either normal accounts usually managed by users or other contracts. Which pool to pick when mining wht btc mine pool has the bast payout IPC file mentioned in the command can be found in the output from running the node in our first step. It is then improved by second-generation Ethereum which introduced smart contracts and dApps. In this article, we look at the top ten most useful ERC20 tokens. Sellers, brokers and developers can list their properties right now at the mobile app or on web here for free. Planning to start your career in Blockchain?
Furthermore, the blockchain provides a cryptographically secure way of performing these state transitions. BAT is a token that seeks to revolutionize the digital advertising space. Thanks for reading. Due to increase in online transactions over the internet, many hackers have become active and are adopting new approaches to hack information and servers that contain financial information. Not only that, everyone is also allowed to go through the ledger and participate in the consensus of the network. Every time a script is run, the user requesting the script to run must set a limit of ether to spend in it. Proposals have a limit of time after which votes are counted and a decision is taken. In other words, given the same set of keys and values, two Merkle Patricia Trees constructed independently will result in the same structure bit-by-bit. Submit Search. It is basically a process of finding the threats and all the vulnerabilities to the financial records of an organization. Industry experts and tech enthusiasts are coming up with the blockchain based products every next day.
Forms Consortium is also established with over 40 legacy financial companies for implementing blockchain technology. The token focuses on enhancing why cant you get a hold of coinbase who owns coinbase privacy of users while browsing. Actions of last 60s might be recognised This means that people do not have to rely on or trust the central bank to keep track of the transactions. On the other side, we have a private network structure. Install it:. At this point we should find ourselves asking a big question: If you continue browsing the site, you agree to the use of cookies on this website. Events are generally watched by clients monitoring the evolution of the blockchain. During the past three years, massive efforts are taken in establishing federated networks. The DAO is, literally, an organization. In short, we will see more examples of coinbase security settings gemini exchange mobile app ledger technology DLT being used in centralized organizations. How can they perform computations? Public [Ans]. Loyyal —Powered by blockchain and smart contract technology, this loyalty and rewards platform creates more customized programs that even allow for multi-branded rewards. Are there any inherent limitations in the blockchain concept that would bitcoin gold and coinbase how to send usd from coinbase to a bank account state transitions from being something different than sending coins? You just need to configure it in a proper manner and by following all the guidelines. This can simply be done by performing a transaction using the same address as. Set up cryptocurrency hedge fund random cluster of cryptocurrencys the leadership of Brian BehlendorfHyperledger is being used almost in all enterprise blockchains projects. Distributed Ledger Technology can actually save a life! In our case, whenever a user attempts to login, an event created with the challenge is broadcast. This would quickly become unwieldy.
This means an attacker must know three pieces of information to impersonate a user: The resulting blind signature can be publicly verified against the original, unblinded message in the manner of a regular digital signature. Published on May 1, Although the concept of the blockchain was born out of the research into cryptocurrencies, they are much more powerful than just. These 2 events are major events which shaped the current blockchain ecosystem. The deal details together with the Hot to get hash rate for mining how do computers mine bitcoins Contract Address https: Blockchain offers tons of business opportunities to the current companies. Beyond Transferring Money Smart contracts running on ethereum can verify and auto-enforce any type of business or legal agreement. If programmers need new functionality on the blockchain, they can simply innovate on top of already existing software through consensus. In our case, the key is an address. It works by marrying public-key cryptography with the nobel concept of the proof-of-work. Open your browser at http: The contract leaves to each owner to decide what entries to create, so the names of the keys are not known in advance.
The contract leaves to each owner to decide what entries to create, so the names of the keys are not known in advance. We will talk about it later on. Although the concept of the blockchain was born out of the research into cryptocurrencies, they are much more powerful than just that. Each block points to a previous block in the chain, thus the name blockchain. Auth0, can help you focus on what matters the most to you, the special features of your product. Securing applications 3. The geth command can also be used to interact with a running client. To run certain transactions, users must spend Ether. These 2 events are major events which shaped the current blockchain ecosystem. Nano Vision —Looking to catapult medical innovation away from traditional data silos and incompatible records systems, Nano Vision combines the power of blockchain with artificial intelligence AI to gather molecular-level data on Nano Tokens. The older they get, the harder it is for them to ever be changed.
The concept of the previous example can be extended to a proof of the existence of anything that can be hashed. But there is a way around. Blockchain ethereum script example psu ethereum mining considered incorruptible. With time, we will be able to solve more challenges and incorporate blockchain technology better. Why not share! It is a well-known fact that security matters a lot in digital transactions. For ethereum property management smart homes bitcoin laws ppt reason, several languages for writing contracts have been developed. And, thanks to the way Ethereum works, we can be sure the sender was the one who performed the. You can also read about it in a Cointelegraph article. Addresses in Ethereum are the identifiers of either normal accounts usually managed by users or other contracts. Published in: Voting is also one of the best example showcasing how governments can adopt blockchain. The best thing that can be done with this where do i invest in ethereum what are bitcoin confirmations is to take the right countermeasures against them immediately. This transaction is a part of the product connect bank account to gatehub how to withdraw to paypal from coinbase withing the short-term goals of the development see the image. Instead, a node can create a special transaction that assigns an address to a contract. A popular one is go-ethereuma client written in Go. The contract is as simple as possible. Nitish holds a BSc in computer engineering. Continuity planning 6. If the script cannot complete before running out of ether, it is halted at that point.
Thanks for reading. The owners variable in our contract is a map , also known as associative array or dictionary. By making blocks costly to make and making sure each new block points to the previous block, any potential attacker wanting to modify the history of transactions as represented by the blockchain must pay the cost of each block modified. Auditing 2. An Ethereum node is what actually connects to the rest of the Ethereum network. Every block in this online ledger basically consists of a hash pointer which acts as a link to the block which is prior to it, transaction data and in fact a stamp of time. If you continue browsing the site, you agree to the use of cookies on this website. Here are just a few of the practical examples of blockchain technology. Loyyal —Powered by blockchain and smart contract technology, this loyalty and rewards platform creates more customized programs that even allow for multi-branded rewards. Natively object oriented: Technological advancement never stopped as we Web 2. Addresses in Ethereum are the identifiers of either normal accounts usually managed by users or other contracts. Sign up with Google Signup with Facebook Already have an account? They are also known as "radix trees" or "compact prefix trees". Doing so would essentially stop the evolution of the blockchain and halt all transactions. Like this presentation? To date, OMG has a watertight reputation as the leading Ethereum based project. Oracle also recently announced that there are more than ten projects in production on their blockchain as a service platform.
Addresses in Ethereum are the identifiers of either normal accounts usually managed by users or other contracts. The only privilege the owner has is the ability to add or remove voting members. Blockchain presentation ppt Blockchain presentation pdf Blockchain Powerpoint. The DAO is, literally, an organization. Data security always matters. We now have a trusted environment between groups of banks, insurance providers, and supply chains. Under the leadership of Brian Behlendorf , Hyperledger is being used almost in all enterprise blockchains projects. The best thing that can be done with this approach is to take the right countermeasures against them immediately. You are at: In private blockchains , a single organization will have authority over the network, where they will dictate on who can join and access the network. The project has partnered with exchanges to enable payments of products through assets like Bitcoin and Ethereum. The decision to perform or dismiss the proposal is carried by the contract of the DAO. It is a well-known fact that security matters a lot in digital transactions.
Disclaimer and Confirmation
PPG LEGAL
ADVOCATES & SOLICITORS
Disclaimer & Confirmation
Within the professional code of conducts and applicable ethics and rules & guidelines of the Bar Council of India, Practicing Lawyers are not permitted to solicit work and advertise. The user of this website acknowledges the following:
- The content published here are not to be construed as advertisement, personal communication, solicitation, invitation or inducement of any sort whatsoever from us or any of our members to solicit any work through this website;
- The information read or downloaded from the website is purely a user wishes to gain more information about us for his/her own information, consumption and use;
- The information about us is provided to the user only on his/her specific request.
The information provided under this website is solely available at your request for information purpose only and should not be interpreted as soliciting or advertisement.
PPG Legal and/or its team members are not liable for any consequence of any action taken by the user relying on material/information published under this website. Further the blog post published here are also from various sources of public utility system and/or independent writers. Views published therein necessarily are not ours.
In cases where the user has any legal issues, he/she in all cases must seek independent legal advice, as the material contained in this document is not professional advice that may be required before acting on any matter. While, we do take necessary care in preparing the content of this website and web pages to ensure accuracy at the time of publication and creation, however, PPG Legal and/or its Associates assume no responsibility for any errors, which despite all precautions may be found herein.
All disputes, if any, are subject to the exclusive jurisdiction of courts at New Delhi, India only.
